Submitted:
02 December 2025
Posted:
02 December 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Related Surveys
1.2. Contributions of This Work
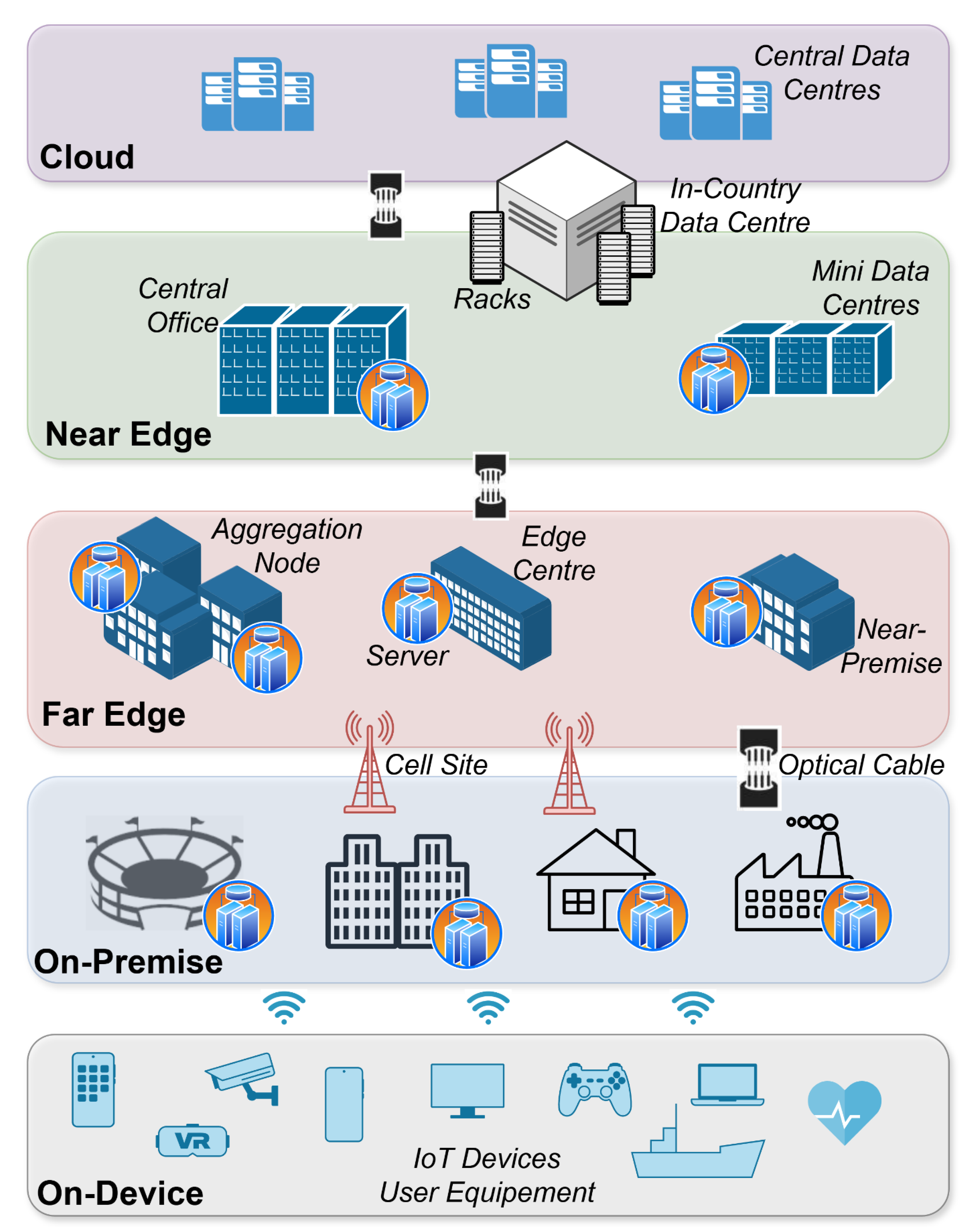
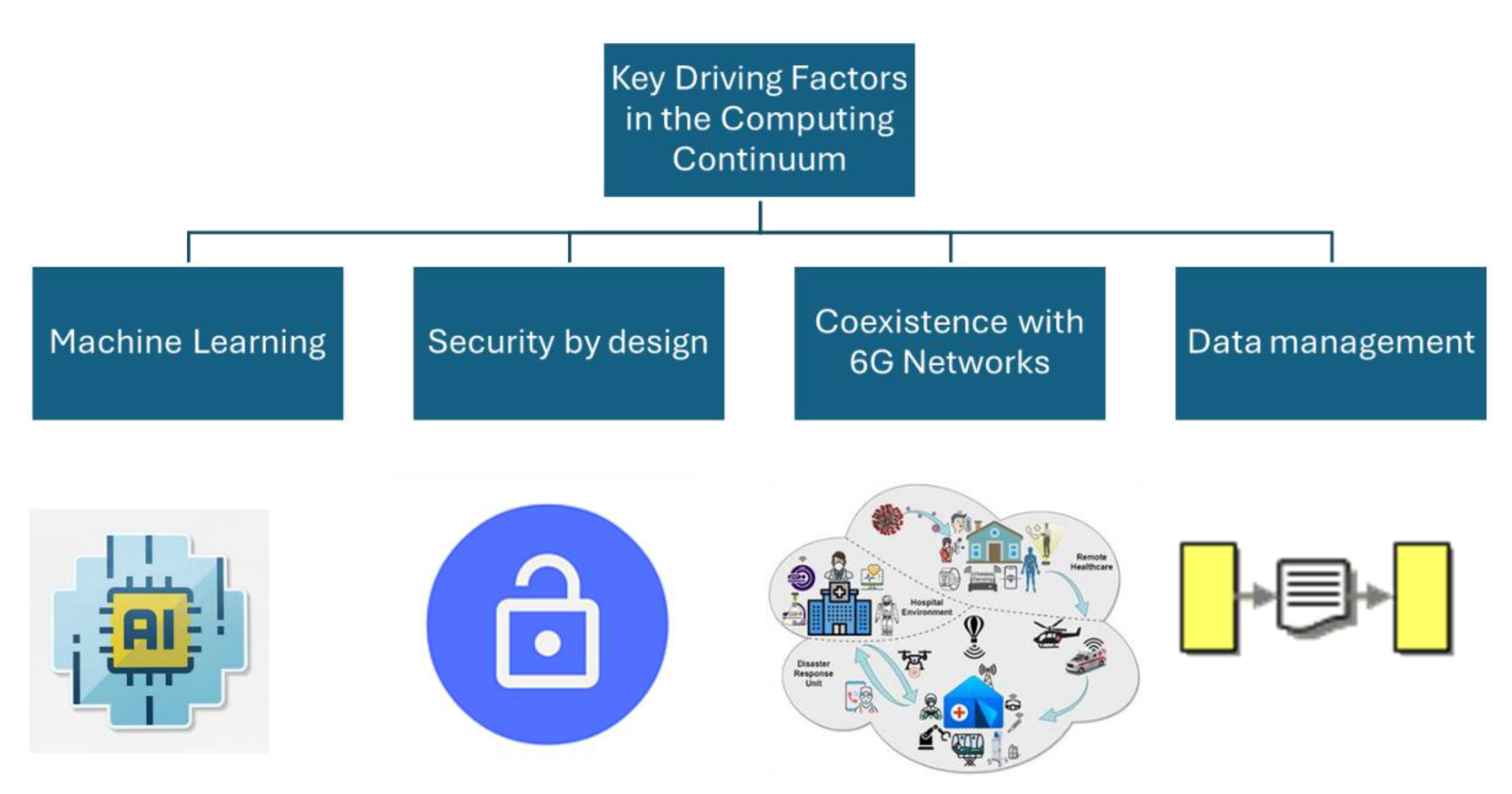
2. Key Driving Factors
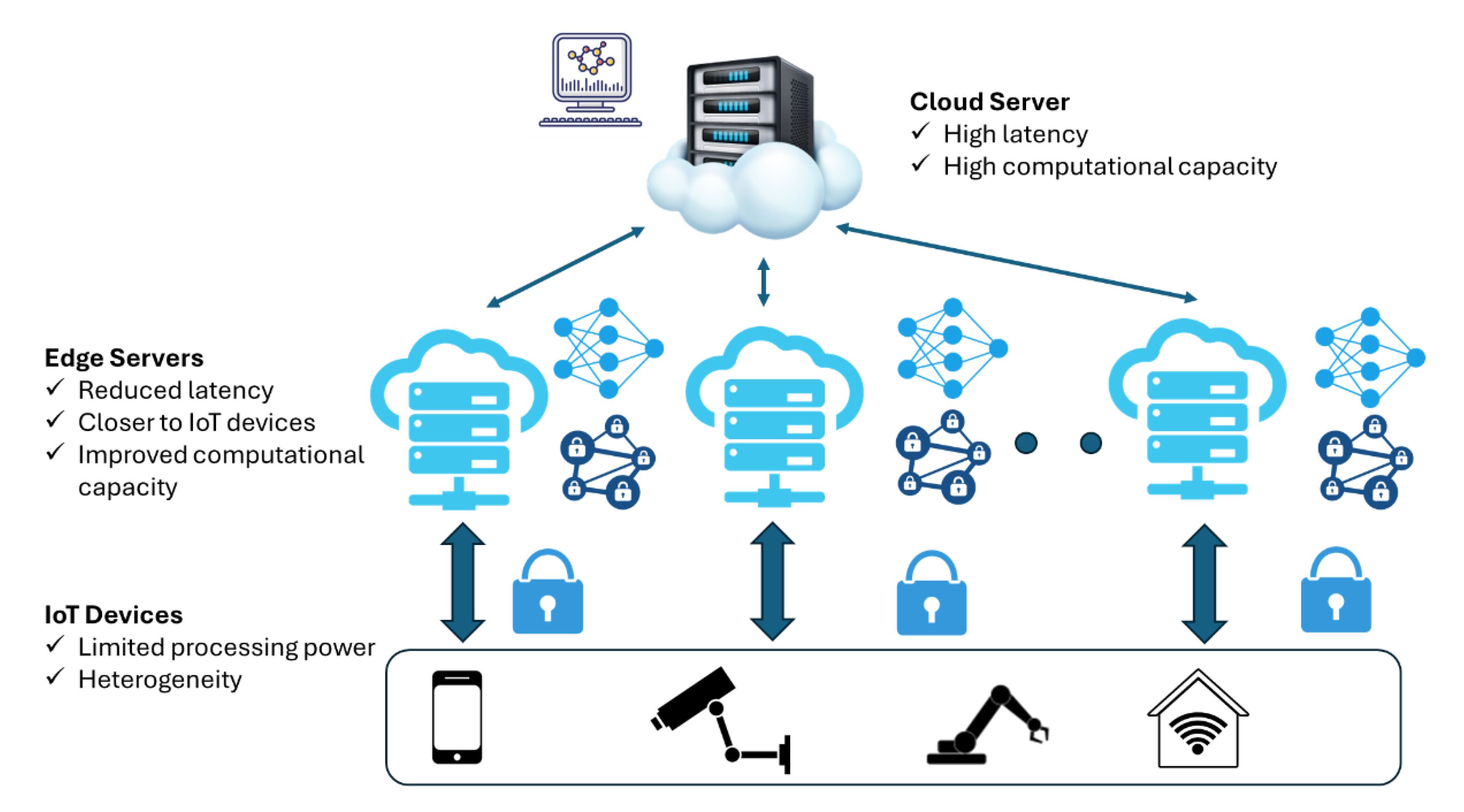
2.1. Machine Learning
2.2. Security by Design
2.3. Coexistence with 6G Networks
2.4. Data Management
3. Related Works
4. Discussion - Open Issues and Key Challenges
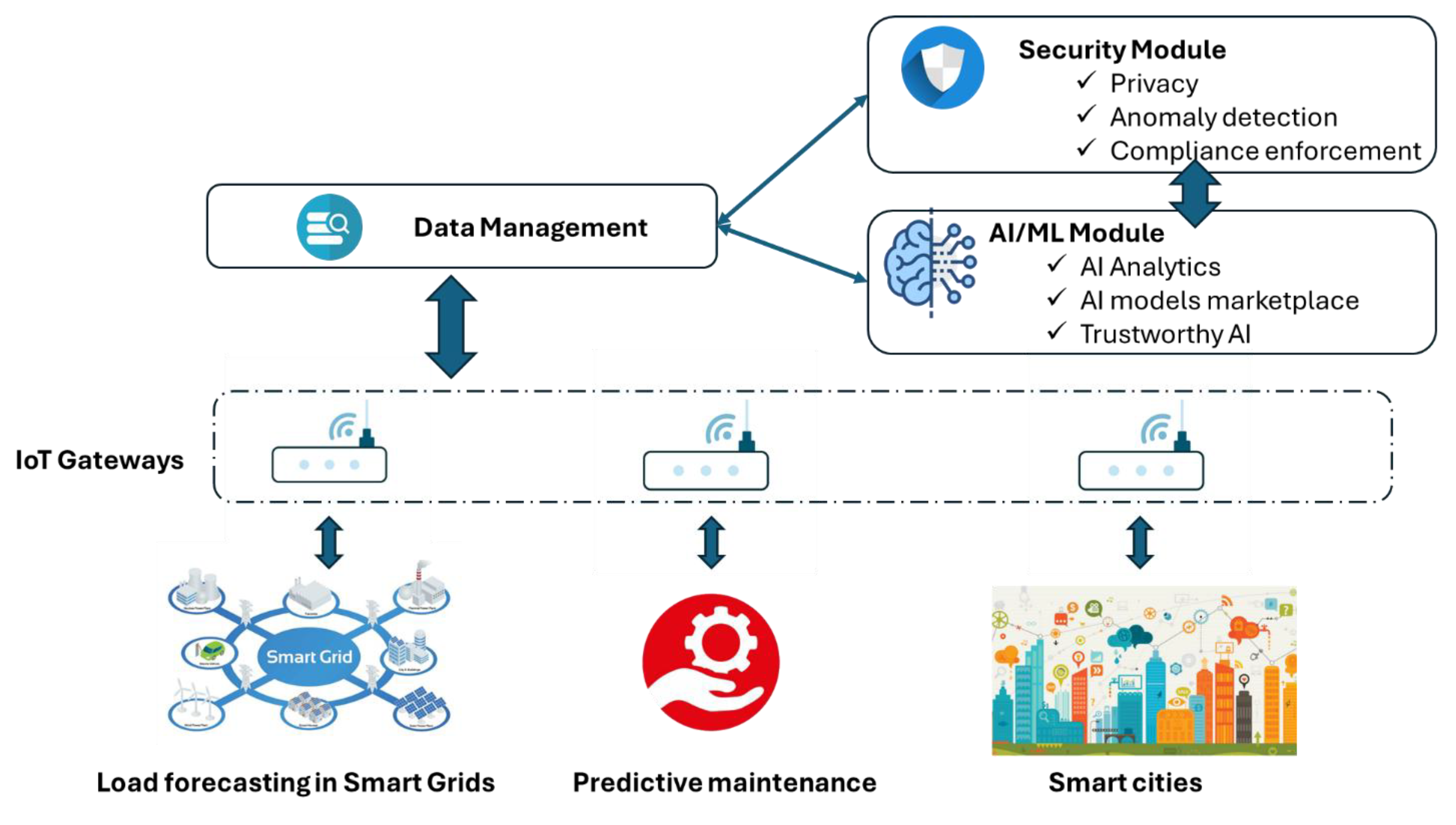
5. Potential Use Cases
5.1. Predictive Maintenance in Industrial 4.0 Scenarios
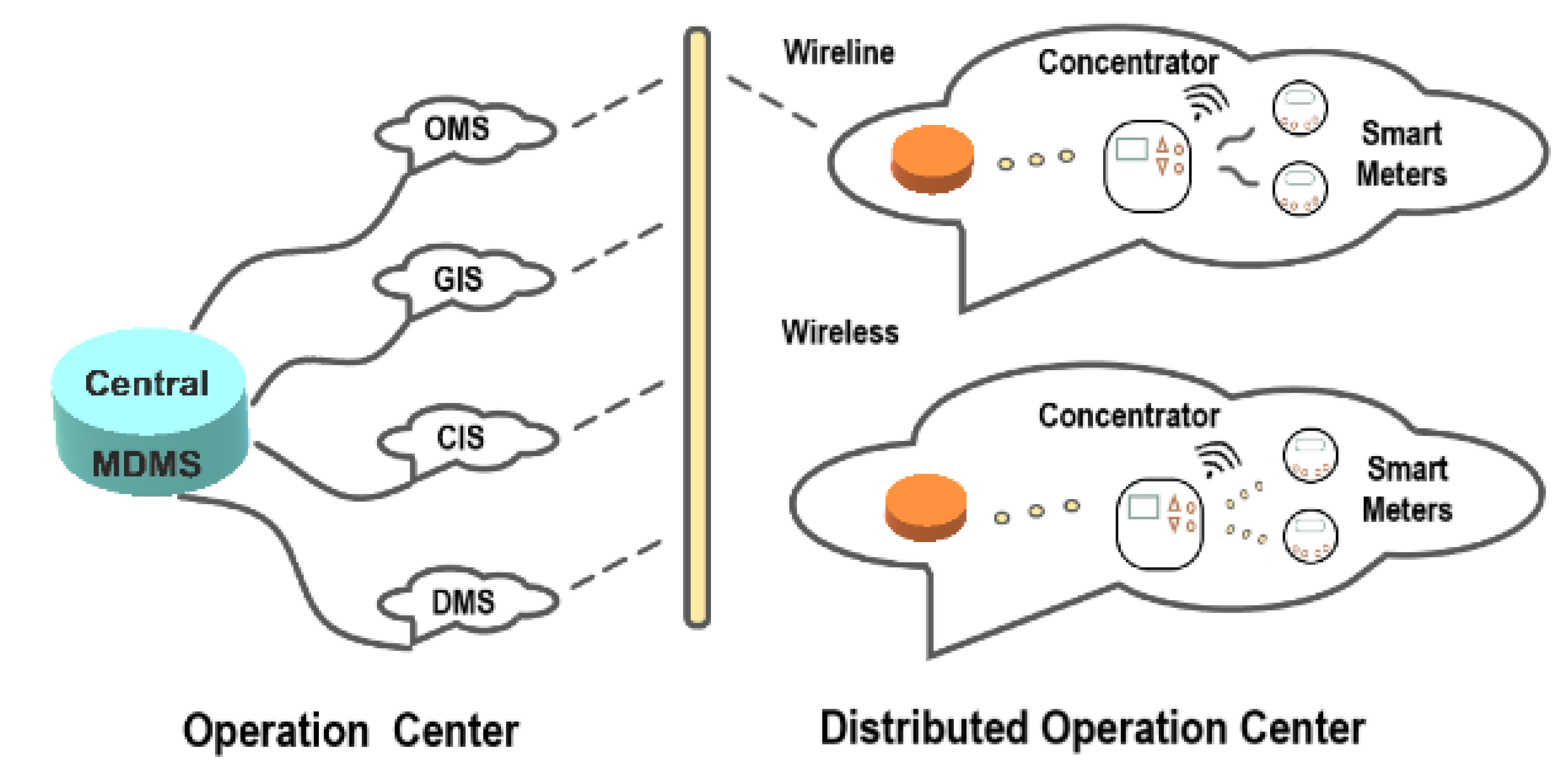
5.2. Load Forecasting in Smart Grid Environments
5.3. Smart Cities
5.4. Infrastructure Monitoring
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| 6G | Sixth Generation |
| 6GCC | 6G Computing Continuum (6GCC) |
| AI | Artificial Intelligence |
| AIoT | Artificial Intelligence of Things (AIoT) |
| AP | Access Point |
| API | Application Programming Interface |
| AppDev | Application Developer |
| AppInt | Application Integrator |
| CEC | Cloud Edge Continuum |
| CIS | Customer Information System |
| CP | Cloud Provider |
| DCS | Distributed Computing System |
| DMM | Data Management Module |
| DMS | Data Management System |
| DRL | Deep Reinforcement Learning |
| ECPP | Edge Cloud Platform Provider |
| EU | European Union |
| GIS | Geographical Information System |
| FL | Federated Learning |
| HW | Hardware |
| IM | Intelligence Module |
| IoT | Internet of Things |
| IoTinuum | IoT Computing Continuum |
| IoTP | IoT Provider |
| IEC | IoT Edge Cloud |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| NFV | Network Function Virtualization |
| NN | Neural Network |
| NP | Network Provider |
| OS | Operating System |
| RL | Reinforcement Learning |
| PaaS | Platform as a Service |
| PoP | Point of Presence |
| PUF | Physical Unclonable Function |
| QoS | Quality of Service |
| SaS | Security as a Service |
| SBA | Service Based Architecture |
| SDN | Software Defined Networking |
| SDS | Self-Distribution Systems |
| TL | Transfer Learning |
References
- Abdulhussain, S.H.; Mahmmod, B.M.; Alwhelat, A.; Shehada, D.; Shihab, Z.I.; Mohammed, H.J.; Abdulameer, T.H.; Alsabah, M.; Fadel, M.H.; Ali, S.K.; et al. A Comprehensive Review of Sensor Technologies in IoT: Technical Aspects, Challenges, and Future Directions. Computers 2025, 14, 342. [Google Scholar] [CrossRef]
- Adam, M.; Hammoudeh, M.; Alrawashdeh, R.; Alsulaimy, B. A Survey on Security, Privacy, Trust, and Architectural Challenges in IoT Systems. IEEE Access 2024, vol. 12, 57128–57149. [Google Scholar] [CrossRef]
- Behnke, I; Austad, H. Real-Time Performance of Industrial IoT Communication Technologies: A Review. IEEE Internet of Things Journal 2024, 11(5), 7399–7410. [Google Scholar] [CrossRef]
- Folgado, F.J.; Calderón, D.; González, I.; Calderón, A.J. Review of Industry 4.0 from the Perspective of Automation and Supervision Systems: Definitions, Architectures and Recent Trends. Electronics 2024, 13, 782. [Google Scholar] [CrossRef]
- Gkonis, P.; Giannopoulos, A.; Trakadas, P.; Masip-Bruin, X.; D’Andria, F. A Survey on IoT-Edge-Cloud Continuum Systems: Status, Challenges, Use Cases, and Open Issues. Future Internet 2023, 15, 383. [Google Scholar] [CrossRef]
- Crespo-Aguado, M.; Lozano, R.; Hernandez-Gobertti, F.; Molner, N.; Gomez-Barquero, D. Flexible Hyper-Distributed IoT–Edge–Cloud Platform for Real-Time Digital Twin Applications on 6G-Intended Testbeds for Logistics and Industry. Future Internet 2024, 16, 431. [Google Scholar] [CrossRef]
- Masip-Bruin, X.; Marín-Tordera, E.; Sánchez-López, S.; Garcia, J.; Jukan, A.; Juan Ferrer, A.; Queralt, A.; Salis, A.; Bartoli, A.; Cankar, M.; et al. Managing the Cloud Continuum: Lessons Learnt from a Real Fog-to-Cloud Deployment. Sensors 2021, 21, 2974. [Google Scholar] [CrossRef]
- Kaftantzis, N.; Kogias, D.G.; Patrikakis, C.Z. Exploring the Impact of Resource Management Strategies on Simulated Edge Cloud Performance: An Experimental Study. Network 2024, 4, 498–522. [Google Scholar] [CrossRef]
- Almutairi, M.; Sheldon, F.T. IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions. Electronics 2025, 14, 1394. [Google Scholar] [CrossRef]
- Ficili, I.; Giacobbe, M.; Tricomi, G.; Puliafito, A. From Sensors to Data Intelligence: Leveraging IoT, Cloud, and Edge Computing with AI. Sensors 2025, 25, 1763. [Google Scholar] [CrossRef]
- Cajas Ordóñez, S.A.; Samanta, J.; Suárez-Cetrulo, A.L.; Carbajo, R.S. Intelligent Edge Computing and Machine Learning: A Survey of Optimization and Applications. Future Internet 2025, 17, 417. [Google Scholar] [CrossRef]
- Elhanashi, A.; Dini, P.; Saponara, S.; Zheng, Q. Advancements in TinyML: Applications, Limitations, and Impact on IoT Devices. Electronics 2024, 13, 3562. [Google Scholar] [CrossRef]
- Vaño, R.; Lacalle, I.; Sowiński, P.; S-Julián, R.; Palau, C.E. Cloud-Native Workload Orchestration at the Edge: A Deployment Review and Future Directions. Sensors 2023, 23, 2215. [Google Scholar] [CrossRef]
- The Kube Edge. Available online: https://kubeedge.io/.
- Prangon, N.F.; Wu, J. AI and Computing Horizons: Cloud and Edge in the Modern Era. J. Sens. Actuator Netw. 2024, 13, 44. [Google Scholar] [CrossRef]
- Donta, P.K.; Murturi, I.; Casamayor Pujol, V.; Sedlak, B.; Dustdar, S. Exploring the Potential of Distributed Computing Continuum Systems. Computers 2023, 12, 198. [Google Scholar] [CrossRef]
- Bittencourt, L. F.; Rodrigues-Filho, R.; Spillner, J.; De Turck, F.; Pereira dos Santos, J. P.; da Fonseca, N. L. S.; Rana, O.; Parashar, M.; Foster, I. The computing continuum: past, present, and future. Computer Science Review 2025, vol. 58, 100782. [Google Scholar] [CrossRef]
- Kazi, B.U.; Islam, M.K.; Siddiqui, M.M.H.; Jaseemuddin, M. A Survey on Software Defined Network-Enabled Edge Cloud Networks: Challenges and Future Research Directions. Network 2025, 5, 16. [Google Scholar] [CrossRef]
- Giannopoulos, A.; Paralikas, I.; Spantideas, S.; Trakadas, P. COOLER: Cooperative Computation Offloading in Edge-Cloud Continuum Under Latency Constraints via Multi-Agent Deep Reinforcement Learning. 2024 International Conference on Intelligent Computing, Communication, Networking and Services (ICCNS); 2024, pp. 9–16. [CrossRef]
- Ros, S.; Ryoo, I.; Kim, S. DRL-Driven Intelligent SFC Deployment in MEC Workload for Dynamic IoT Networks. Sensors 2025, 25, 4257. [Google Scholar] [CrossRef]
- Liberti, F.; Berardi, D.; Martini, B. Federated Learning in Dynamic and Heterogeneous Environments: Advantages, Performances, and Privacy Problems. Appl. Sci. 2024, 14, 8490. [Google Scholar] [CrossRef]
- Dawood, M.; Tu, S.; Xiao, C.; Alasmary, H.; Waqas, M.; Rehman, S.U. Cyberattacks and Security of Cloud Computing: A Complete Guideline. Symmetry 2023, 15. [Google Scholar] [CrossRef]
- Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Zabidi, S.A.; Bin Najeeb, A.R.; Kabbani, A. A Survey on Edge Computing (EC) Security Challenges: Classification, Threats, and Mitigation Strategies. Future Internet 2025, 17, 175. [Google Scholar] [CrossRef]
- Tripi, G.; Iacobelli, A.; Rinieri, L.; Prandini, M. Security and Trust in the 6G Era: Risks and Mitigations. Electronics 2024, 13, 2162. [Google Scholar] [CrossRef]
- Kazmi, S.H.A.; Hassan, R.; Qamar, F.; Nisar, K.; Ibrahim, A.A.A. Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions. Symmetry 2023, 15, 1147. [Google Scholar] [CrossRef]
- Bast, C.; Yeh, K.-H. Emerging Authentication Technologies for Zero Trust on the Internet of Things. Symmetry 2024, 16, 993. [Google Scholar] [CrossRef]
- Chataut, R.; Nankya, M.; Akl, R. 6G Networks and the AI Revolution—Exploring Technologies, Applications, and Emerging Challenges. Sensors 2024, 24, 1888. [Google Scholar] [CrossRef] [PubMed]
- Salameh, A.I.; El Tarhuni, M. From 5G to 6G—Challenges, Technologies, and Applications. Future Internet 2022, 14, 117. [Google Scholar] [CrossRef]
- Adeogun, R.; Berardinelli, G.; Mogensen, P.E.; Rodriguez, I.; Razzaghpour, M. Towards 6G in-X subnetworks with sub-millisecond communication cycles and extreme reliability. IEEE Access 2020, 8, 110172–110188. [Google Scholar] [CrossRef]
- Berardinelli, G.; Adeogun, R. Hybrid radio resource management for 6G subnetwork crowds. IEEE Commun. Mag. 2023, 61, 148–154. [Google Scholar] [CrossRef]
- Corici, M. – I.; et al. Organic 6G Networks: Vision, Requirements, and Research Approaches. IEEE Access 2023, vol. 11, 70698–70715. [Google Scholar] [CrossRef]
- Judvaitis, J.; Blumbergs, E.; Arzovs, A.; Mackus, A.I.; Balass, R.; Selavo, L. A Set of Tools and Data Management Framework for the IoT–Edge–Cloud Continuum. Appl. Syst. Innov. 2024, 7, 130. [Google Scholar] [CrossRef]
- Karagiannis, V. Data Sovereignty and Compliance in the Computing Continuum. 2024 11th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria; pp. 123–130. [CrossRef]
- Nedoshivina, L.; Levacher, K.; Fraser, K.; Halimi, A.; Braghin, B. AI-driven Workload Management in Meta OS. In Proceedings of the 1st International Workshop on MetaOS for the Cloud-Edge-IoT Continuum (MECC 2024); Association for Computing Machinery : New York, NY, USA; pp. 14–20. [CrossRef]
- The FLUIDOS project. Available online: https://fluidos.eu/.
- Verginadis, Y.; et al. NebulOuS: A Meta-Operating System with Cloud Continuum Brokerage Capabilities. Eighth International Conference on Fog and Mobile Edge Computing (FMEC), Tartu, Estonia, 2023 ; pp. 254–261. [Google Scholar] [CrossRef]
- The NebulOus project. Available online: https://nebulouscloud.eu/.
- NEMO: Building the Next Generation Meta Operating System.
- The NEMO project. Available online: https://meta-os.eu/.
- Kamienski, C.; Zyrianoff, I.; Bittencourt, L. F.; Di Felice, M. IoTinuum: The IoT Computing Continuum. 2024 20th International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT), Abu Dhabi, United Arab Emirates, 2024 ; pp. 732–739. [Google Scholar] [CrossRef]
- Tärneberg, W.; et al. The 6G Computing Continuum (6GCC): Meeting the 6G computing challenges. 1st International Conference on 6G Networking (6GNet), Paris, France, 2022 ; pp. 1–5. [Google Scholar] [CrossRef]
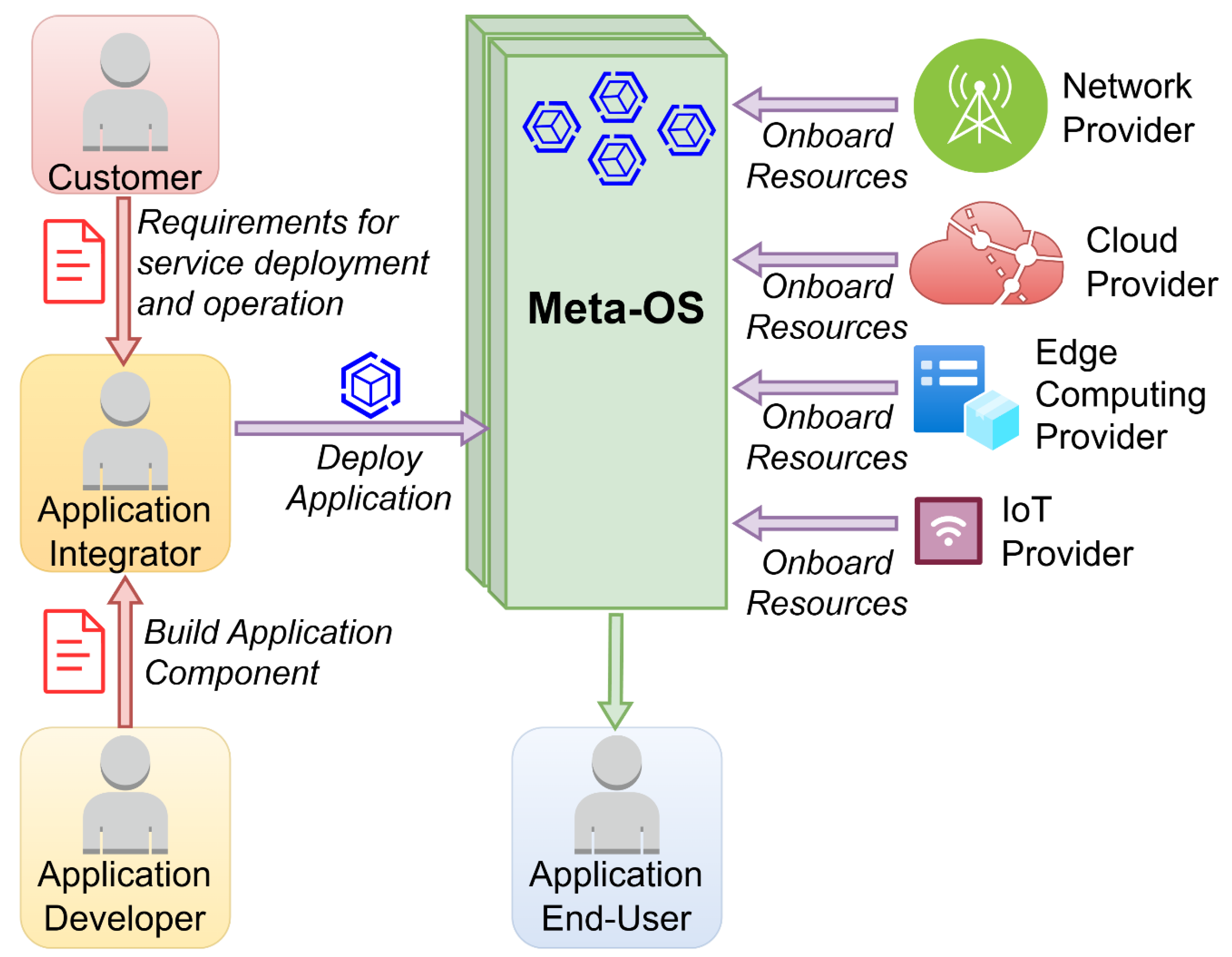
- Trakadas, P.; Masip-Bruin, X.; Facca, F.M.; Spantideas, S.T.; Giannopoulos, A.E.; Kapsalis, N.C.; Martins, R.; Bosani, E.; Ramon, J.; Prats, R.G.; et al. A Reference Architecture for Cloud–Edge Meta-Operating Systems Enabling Cross-Domain, Data-Intensive, ML-Assisted Applications: Architectural Overview and Key Concepts. Sensors 2022, 22, 9003. [Google Scholar] [CrossRef]
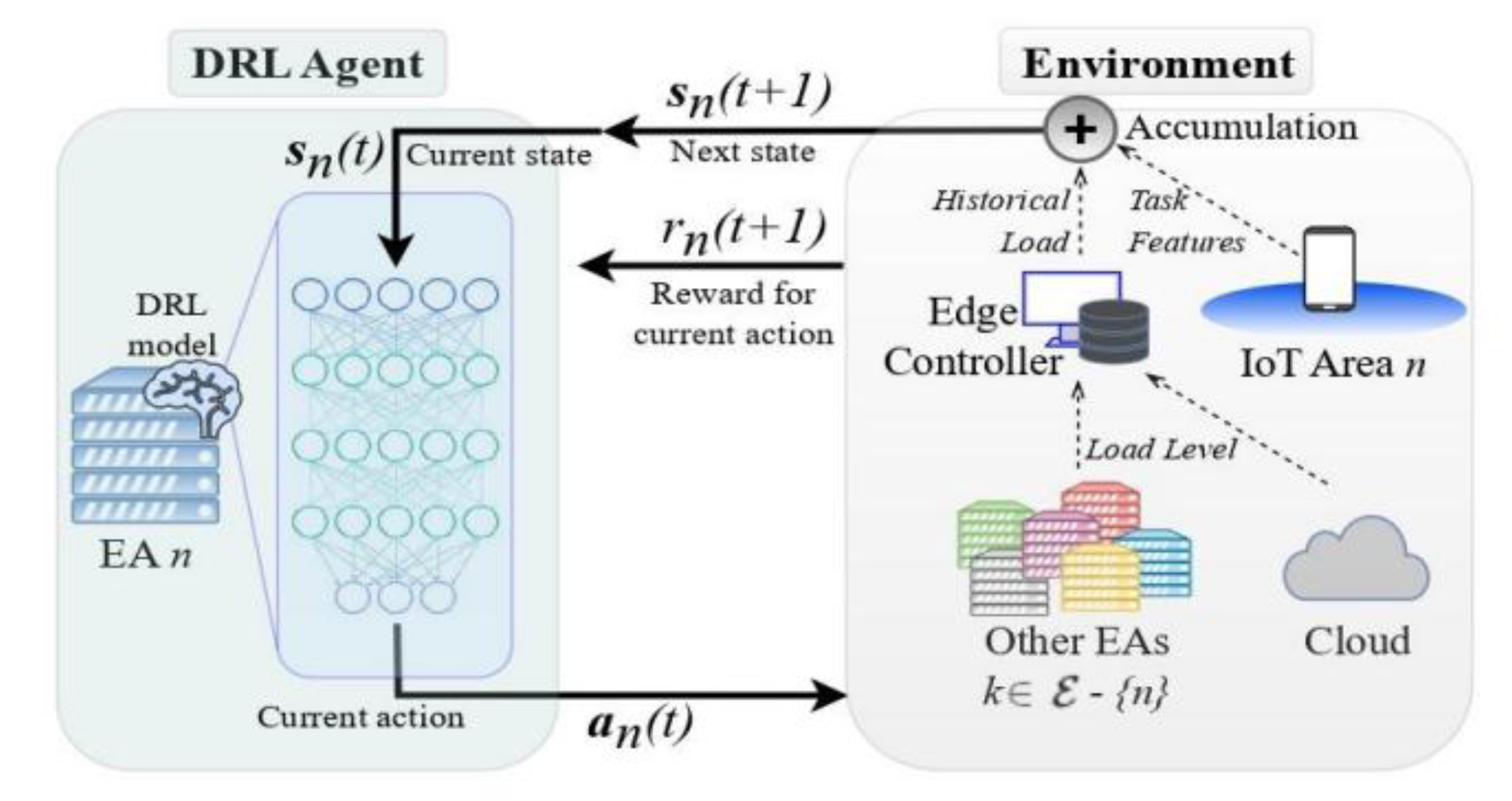
- Giannopoulos, A. E.; Paralikas, I.; Spantideas, S. T.; Trakadas, P. HOODIE: Hybrid Computation Offloading via Distributed Deep Reinforcement Learning in Delay-Aware Cloud-Edge Continuum. IEEE Open Journal of the Communications Society 2024, 5, 7818–7841. [Google Scholar] [CrossRef]
- Skianis, K.; Giannopoulos, A.; Gkonis, P.; Trakadas, P. Data Aging Matters: Federated Learning-Based Consumption Prediction in Smart Homes via Age-Based Model Weighting. Electronics 2023, 12, 3054. [Google Scholar] [CrossRef]
- Garcia, J.; Masip-Bruin, X.; Giannopoulos, A.; Trakadas, P.; Ordoñez, S. A. C.; Samanta, J.; D’Andria, F. ICOS: An Intelligent MetaOS for the Continuum. In Proceedings of the 2nd International Workshop on MetaOS for the Cloud-Edge-IoT Continuum, 2025 ; pp. 53–59. [Google Scholar] [CrossRef]
- Filho, R. R.; et al. A Self-Distributing System Framework for the Computing Continuum. 32nd International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 2023 ; pp. 1–10. [Google Scholar] [CrossRef]
- Rahman, A. B.; Charatsaris, P.; Tsiropoulou, E. E.; Papavassiliou, S. Symbiotic Resource Pricing in the Computing Continuum Era. IEEE Transactions on Mobile Computing 2025, 24(7), 6474–6487. [Google Scholar] [CrossRef]
- Sturley, H.; Fournier, A.; Salcedo-Navarro, A.; Garcia-Pineda, M.; Segura-Garcia, J. Virtualization vs. Containerization, a Comparative Approach for Application Deployment in the Computing Continuum Focused on the Edge. Future Internet 2024, 16, 427. [Google Scholar] [CrossRef]
- Roumeliotis, A.J.; Myritzis, E.; Kosmatos, E.; Katsaros, K.V.; Amditis, A.J. Multi-Area, Multi-Service and Multi-Tier Edge-Cloud Continuum Planning. Sensors 2025, 25, 3949. [Google Scholar] [CrossRef]
- Al-Dulaimy, A. The computing continuum: From IoT to the cloud. Internet of Things 2024, vol. 27, 101272. Available online: https://www.sciencedirect.com/science/article/pii/S2542660524002130. [CrossRef]
- Rossini, R.; et al. Open Source in NExt Generation Meta Operating Systems (NEMO). 2024 9th International Conference on Smart and Sustainable Technologies (SpliTech), Bol and Split, Croatia, 2024 ; pp. 1–5. [Google Scholar] [CrossRef]
- Barbareschi, M.; Casola, V.; Lombardi, D. Ensuring End-to-End Security in Computing Continuum Exploiting Physical Unclonable Functions. 2023 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Naples, Italy, 2023; pp. 273–278. [Google Scholar] [CrossRef]
- Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Zabidi, S.A.; Bin Najeeb, A.R.; Kabbani, A. Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks. Future Internet 2025, 17, 275. [Google Scholar] [CrossRef]
- Chef Software DevOps Automation Solutions | Chef. Available online: https://www.chef.io/.
- Damian, A. I. Ratio1 meta-OS - decentralized MLOps and beyond. 2025 25th International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania; pp. 258–265. [CrossRef]
- Shah, Q.A.; Shafi, I.; Ahmad, J.; Alfarhood, S.; Safran, M.; Ashraf, I. A Meta Modeling-Based Interoperability and Integration Testing Platform for IoT Systems. Sensors 2023, 23, 8730. [Google Scholar] [CrossRef] [PubMed]
- Petrakis, K.; Agorogiannis, E.; Antonopoulos, G.; Anagnostopoulos, T.; Grigoropoulos, N.; Veroni, E.; Berne, A.; Azaiez, S.; Benomar, Z.; Kakoulidis, H.; et al. Enhancing DevOps Practices in the IoT–Edge–Cloud Continuum: Architecture, Integration, and Software Orchestration Demonstrated in the COGNIFOG Framework. Software 2025, 4, 10. [Google Scholar] [CrossRef]
- The COGNIFOC Project. Available online: https://cognifog.eu/.
- Iman, M.; Arabnia, H.R.; Rasheed, K. A Review of Deep Transfer Learning and Recent Advancements. Technologies 2023, 11, 40. [Google Scholar] [CrossRef]
- Heydari, S.; Mahmoud, Q.H. Tiny Machine Learning and On-Device Inference: A Survey of Applications, Challenges, and Future Directions. Sensors 2025, 25, 3191. [Google Scholar] [CrossRef]
- Nomikos, N.; Xylouris, G.; Patsourakis, G.; Nikolakakis, V.; Giannopoulos, A.; Mandilaris, C.; Gkonis, P.; Skianis, C.; Trakadas, P. A Distributed Trustable Framework for AI-Aided Anomaly Detection. Electronics 2025, 14, 410. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, Y.; Jiang, J. Blockchain-Based Distributed Computing Consistency Verification for IoT Mobile Applications. Appl. Sci. 2023, 13, 7762. [Google Scholar] [CrossRef]
- Barona López, L.I.; Borja Saltos, T. Heterogeneity Challenges of Federated Learning for Future Wireless Communication Networks. J. Sens. Actuator Netw. 2025, 14, 37. [Google Scholar] [CrossRef]
- Trakadas, P.; Sarakis, L.; Giannopoulos, A.; Spantideas, S.; Capsalis, N.; Gkonis, P.; Karkazis, P.; Rigazzi, G.; Antonopoulos, A.; Cambeiro, M.A.; et al. A Cost-Efficient 5G Non-Public Network Architectural Approach: Key Concepts and Enablers, Building Blocks and Potential Use Cases. Sensors 2021, 21, 5578. [Google Scholar] [CrossRef]
- Lea, R.; Adame, T.; Berne, A.; Azaiez, S. The Internet of Things, Fog, and Cloud Continuum: Integration Challenges and Opportunities for Smart Cities. Future Internet 2025, 17, 281. [Google Scholar] [CrossRef]
- Ożadowicz, A. Generic IoT for Smart Buildings and Field-Level Automation—Challenges, Threats, Approaches, and Solutions. Computers 2024, 13, 45. [Google Scholar] [CrossRef]
| Paper | Year | Key Directions | Limitations and Open Issues |
|---|---|---|---|
| [5] | 2023 | IoT-Edge-Cloud Systems | Focus is on IEC systems and not on access or data management architectures in the continuum |
| [13] | 2023 | Cloud Edge orchestration at the edge | Evaluation of containerization or virtualization in real world scenarios |
| [15] | 2024 | AI on the edge | Cloud – Edge orchestration Hardware integration to support advanced AI/ML applications |
| [16] | 2023 | Architecture of distributed computing systems |
Learning Models Intelligent protocols for effective resource management |
| [17] | 2025 | Recent trends in computing continuum systems |
Flexible resource allocation Mobility in the continuum |
| [18] | 2025 | SDN and NFV in cloud edge orientations | Performance evaluation in real world orientations |
| Our work | - | Architectural approaches of meta-OSs for the computing continuum | - |
| Paper | Year | Key Directions | Limitations and Open Issues |
|---|---|---|---|
| [34] | 2024 | Presentation of the FLUIDOS Project AI optimization during application execution |
Deployment in real-world scenarios |
| [36] | 2023 | Presentation of the NebulOus project | Performance evaluation in real world scenarios |
| [38] | 2024 | Presentation of the NEMO Project Open-source components for various features (e.g. AI, security, service and data management) |
Performance evaluation in large scale scenarios |
| [40] | 2024 | Six proposed stages of the IoT Computing Continuum | Integration of programmable network stages |
| [41] | 2022 | 6G Computing Continuum | Integration of the computing continuum with 6G architectural approaches |
| [42] | 2022 | Presentation of the RAMOS concept | Context aware machine learning |
| [43] | 2024 | Task offloading in IoT Cloud Edge scenarios via DRL |
Extension in dynamic topologies Additional performance metrics during optimization |
| [44] | 2023 | Federated learning in IoT scenarios | Evaluation in additional real-world scenarios |
| [46] | 2023 | Application resources distribution in the computing continuum |
Evaluation of the SDS approach in more complex scenarios Scalability |
| [47] | 2025 | Resource pricing in computing continuum |
More diverse user behavior scenarios |
| [48] | 2024 | Virtualization vs. Containerization in the cloud continuum | Performance evaluation of bigger hardware architectures for Edge or Cloud Security issues in both approaches |
| [49] | 2025 | Edge-Cloud Continuum Planning | Integration of AI techniques |
| [50] | 2024 | Edge cloud computing and communication |
Efficient communication technologies for the different parts of the continuum |
| [51] | 2024 | Open-source framework of NEMO project | Performance evaluation in large scale scenarios |
| [52] | 2023 | Physical Unclonable Functions | Evaluation in realistic scenarios |
| [55] | 2025 |
Ratio1 meta-OS Decentralized ML and device authentication |
Additional privacy policies Broader cross-chain interoperability |
| [56] | 2023 | Large scale interconnection of IoT devices | Only one smartphone was used for performance evaluation Additional testing with diverse IoT devices |
| [57] | 2025 | The COGNIFOG framework | Orchestration intelligence Decentralized, privacy-preserving AI training at the edge |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





