1. Introduction
Using cloud computing completely changed how technology works. It lets people get the computer power, storage space they need, whenever they want, from places all over [1,2]. The usual way of using cloud services offers a lot of freedom, yet it runs into some serious problems. Work keeps changing, different things need different computer parts, energy costs grow. We need systems that adjust quickly to these situations [3,4,5]. When people decide where to use things by hand, or use a fixed plan, resources often sit idle, jobs take longer, costs go up. More complex online dangers require strong security built into cloud systems, as demonstrated by several studies.
New studies explore putting smart technology within internet services to fix these problems. Clever computer systems forecast resource needs, handle tasks smartly, adjust security as needed [13,14,15]. The system predicts how much computing power it will need by looking at past usage, current activity, using a type of computer program called Long Short-Term Memory networks [16,17,18]. Autoencoders, with tools for finding unusual activity, offer security that looks ahead. They spot new, hidden attacks that older systems miss [19,20,21]. To manage things well, people use methods like Particle Swarm Optimization, Genetic Algorithms, Clouded Leopard Optimization. These techniques help decide where to put resources, organize work, especially when situations are tricky or changing [22,23,24,25].
This new system uses a cloud setup with four parts. It first senses information, then understands it, makes choices, finally takes action. The system constantly checks how well it’s working, looking at things like processor use, memory, network speed, also the status of virtual machines or containers. This system studies the data, forecasts how much work is coming, notices anything unusual. The decision layer turns discoveries into plans, improving how things are used, when work happens, also how secure everything is. The system puts these plans into action with tools like Kubernetes, OpenStack, or VMware vSphere, building a self-running cycle.
The research tests the system design with a computer model, utilizing CloudSim 6.0, also applying information gathered from Google’s data centers. The findings show things work much better, using fewer resources, managing jobs well, saving power, protecting data, when we move away from older cloud systems. These results show computer systems using artificial intelligence, working with cloud technology, can provide computing services that adjust to demand, function consistently, protect the environment.
2. Related Works
Cloud computing now uses artificial intelligence. This combination improves how well clouds work, keeps them secure, anticipates needs, adjusts to changes, finds the best solutions. Researchers investigated various parts of how these things work together, as shown in several reports [1,2,3,4,5].
Initial research showed machine learning helps forecast cloud needs, it also manages work tasks. Researchers suggested methods, including LSTM, RNN, to predict how much computer power virtual systems need [3,4,5]. Some studies focused on flexible scheduling methods, employing improvements like particle swarm optimization or genetic algorithms, to manage changing tasks effectively.
People study ways to make cloud systems use less electricity, keeping them running well. Using computer programs to predict how busy servers will be, alongside smart power controls, lowers energy consumption without sacrificing performance, according to research [8,9].
AI greatly improves security for things stored online. People built systems using a special technique to spot new dangers in shared cloud environments. These techniques work better than older methods that rely on identifying known threats, offering ways to stop problems before they start [10,11,12,13,14].
New developments combine advanced computer systems with online service control. People suggested AI systems with four parts: they watch things, study the data, make choices, then take action. This idea resembles how the system we looked at works, like other research shows [15,16,17,18]. Smart systems now organize diverse cloud computing resources, borrowing ideas from how swarms behave together, to get work done faster, finishing tasks more quickly [16,17,18].
Some projects also linked artificial intelligence with systems that manage tasks, allowing for immediate use with automated jobs. People built AI schedulers working with OpenStack. They improved Kubernetes controllers using machine learning to forecast needs. Developers created systems to blend different approaches for better workload placement, all to lower expenses [19,20,21,22,23,24,25,26,27,28,29,30].
Researchers explored using technology to improve energy use, also to strengthen security in cloud systems. They showed how forecasting problems, discovering unusual activity both help. Researchers investigated autoencoders, together with federated learning techniques, to protect privacy during security monitoring, according to studies [31,32,33,34,35,36].
People developed systems that mix different techniques like learning by reward, swarm intelligence, genetics, plus optimization to control big cloud setups. These systems adjust to changing demands, diverse resource needs, current conditions [37,38,39,40,41,42,43,44,45,46,47,48].
Detailed studies show computer systems using artificial intelligence in the cloud work better, use less power, offer stronger protection than older systems. Systems working together to watch operations, foresee issues, improve efficiency, then act on their own consistently deliver better results, offering increased dependability [49,50,51,52,53,54,55].
Tests show that using artificial intelligence with cloud systems boosts computer processing, memory usage as much as 20%, speeds up how long tasks take to finish by 20 to 25%, lowers energy use by 15 to 20%, also greatly improves finding security breaches. The findings show using smart technology throughout cloud work, from understanding information to carrying out tasks, really works well [56,57,58,59,60,61,62,63].
3. AI-Embedded Cloud Architecture
This system uses artificial intelligence within its cloud design to change how clouds work. It makes clouds smarter, able to adjust on their own, it manages itself. It includes four main parts: understanding information, thinking about it, making choices, then taking action. Each part is important for making cloud operations work better with artificial intelligence.
Figure 1.
AI Embedded Cloud Architecture.
Figure 1.
AI Embedded Cloud Architecture.
The perception layer watches over the cloud, constantly tracking how the system, programs, perform. It covers how busy the processor is, how much memory the system uses, data transfer speed, space taken on drives, also performance records from programs. We gather information about things like how virtual machines are doing, whether containers are working right, or if there are issues with resources, all as it happens. We use sophisticated sensors, monitoring tools throughout our systems, both real things, digital spaces, to gather detailed information. The system gathers information constantly, using fast data streams, then stores it in databases designed for tracking changes over time. This gives the AI a current, precise view of how things are running. It helps the AI spot developing issues, like unusual activity, before they cause problems or outages.
The thinking part of the system uses machine learning to study information gathered from sensors. It finds trends, then creates forecasts. LSTM networks often predict how much work a system will handle, also how resources get used, by looking at past data alongside what is happening now. We can combine computer systems that process information like the human brain with other systems that map relationships. This helps us study how things connect in complicated setups, like cloud computing, data movement across networks, or how applications are built. The system uses several smart methods to understand changing demands, find unusual activity, foresee problems, do all this quite well. Because it can foresee what will happen, this feature helps people make smart choices. It keeps things like resources, work tasks, security well suited to how the system is now, how it will be soon.
The decision layer changes forecasts into plans for managing the cloud. Programs learn to best arrange virtual machines, containers, choose how tasks run, decide when to add resources, all to improve how quickly things get done, reduce delays, save power, lower expenses. They focus on goals like speed, responsiveness, efficiency, cost. To solve tricky scheduling problems, especially when dealing with many different types of equipment or resources, people also use techniques like Particle Swarm Optimization, Genetic Algorithms, or Clouded Leopard Optimization. These methods help find good solutions for complex situations. The system checks how well past choices worked by looking at current results. This lets it adjust cloud operations automatically, improving them bit by bit.
The execution layer carries out choices using automatic systems. It connects with platforms like Kubernetes, OpenStack, or VMware vSphere to manage containers. It makes sure virtual machines, containers, work, plus rules grow smoothly, move easily, recover from problems, follow company standards. This part works with online services to track performance, record activity, offering a complete view of how things are running, what the system is doing. The execution layer makes choices instantly, completing the cycle of smart operation. It changes forecasts, helpful plans, into actual gains for how well, how consistently, how safely your cloud works. These four parts work together to form a cloud system with artificial intelligence. It adjusts itself, recovers from problems, improves performance, then handles various, changing tasks.
4. AI-Enhanced Functionalities
4.1. Resource Management
Cloud systems using artificial intelligence greatly improve how we handle resources. They forecast needs, refine processes, so we get the most from our computers, data storage, network connections. A key use is deciding where to put virtual machines or containers. A learning system looks at how cloud resources are doing then assigns tasks to machines or containers. It aims for the best speed, quick reactions, while also reducing conflicts over resources. These systems learn from past activity, also from current data, so they can handle new situations effectively.
Supplying the right amount of power is also really important, it helps meet the increasing demand for eco-friendly cloud services. Systems look at past use, server power needs, future work estimates to decide which servers to keep running, switch off, or combine. Smart clouds use their intelligence to change how they share power, cutting down on energy waste while still delivering good performance.
The system automatically adjusts resources based on forecasts, improving how well they are used. These forecasting tools predict when a system will be busy or have free capacity. This helps the system add or remove resources as needed. If the system forecasts a quick increase in use for websites, it will automatically provide more computing resources to manage the activity. This keeps things running smoothly, preventing slowdowns, ensuring promised service levels are met. This system forecasts needs, unlike older methods that adjust only after a workload shifts. Those methods frequently respond with delay.
4.2. Scheduling
It’s tricky to arrange different kinds of tasks on cloud systems. Each task needs a unique amount of computing power, must finish by a specific time, relies on certain resources. These differences create difficulties. Smart scheduling picks the best people for jobs, adjusting as things change with a mix of helpful methods. For example, advanced learning methods figure out the best task order using current system information. Other techniques, like particle swarm optimization or the clever crow algorithm, work to improve speed, efficiency, conserve power all at once.
The system intelligently manages tasks, assigning those needing specific hardware, like artificial intelligence processes or demanding calculations, to the best available equipment. This ensures everything runs smoothly, utilizing resources effectively. The AI scheduler works well with various computer parts. It knows what each part can do, so it speeds up tasks, shortens wait times, boosts how much work the system completes. The system schedules tasks, giving preference to important ones. It changes how resources are used to satisfy agreements, yet treats all jobs equitably.
4.3. Security
Keeping things safe with cloud services gets harder as new dangers appear, many users share systems, work happens in lots of places. Cloud systems use artificial intelligence to build security right into how they work, protecting everything automatically. We check how computers, programs, data centers normally work. This helps us spot anything unusual that could mean someone broke in, a virus is present, or settings are wrong. This system keeps data safe, yet allows different locations to work together to find security problems.
Systems use a special technique to find tricky malware, the kind that changes itself to hide, that older methods usually fail to spot. The system learns typical activity, creates realistic problems, then spots even slight, changing threats.
Using artificial intelligence to verify who gets into systems improves security a lot. Systems learn how people use things, then change access rights to give only what’s needed, keeping everything secure. When unusual activity appears, the system automatically takes steps to protect things. It might end a user’s connection, separate certain data, or require extra verification. This keeps the system safe from people abusing their access, stolen passwords, or anyone trying to get in without permission.
5. Implementation & Results
5.1. Simulation Environment and Dataset
We built a testing setup using CloudSim 6.0 to see how well our new cloud system works. This tool lets us create a model of cloud setups, virtual machines, how jobs get assigned, everything we need for a good test. We tested the system with between fifty to two hundred virtual machines, each with different amounts of processing power, graphics cards, or memory. These virtual machines supported five hundred to five thousand smaller cloud servers that ran a variety of tasks, like websites, tasks involving artificial intelligence, or large data jobs.
We got true resource use data from Google’s data center information, showing how systems behave when actively working. This collection of data shows how much processing power, memory, plus input/output resources thousands of jobs use, tracked over time. This helps computer programs understand how things usually happen. We first tested the system using CloudSim's standard scheduling methods with fixed resource limits. Then, we added artificial intelligence to the system. This version used forecasting, improved choices, to operate more effectively.
5.2. AI Models and Integration
We added three main AI parts to the online system
A computer program learned to decide where to put virtual machines or containers. It looked at how busy the system was, checking things like processor use, memory use, network activity, the number of tasks waiting. Using this information, it picked the best placement for each virtual machine or container. The system scored performance based on how quickly it worked, how well it used available tools, how much power it conserved.
We used a special type of computer program, built with a memory system, to learn from past workload patterns. This helped us figure out when demand would quickly increase in the near future. Predictions helped systems automatically adjust, avoiding service disruptions, with resources available when needed.
Autoencoders, a type of computer program, watched system data. They found unusual patterns, suggesting problems or possible security issues, without needing prior examples of what is normal. This tool helped typical security systems find hidden or changing problems.
We put the software components into the central computer system. This created a cycle where forecasts, problem solving steps, were constantly used to improve how things operated.
5.3. Results and Discussion
Resource Utilization
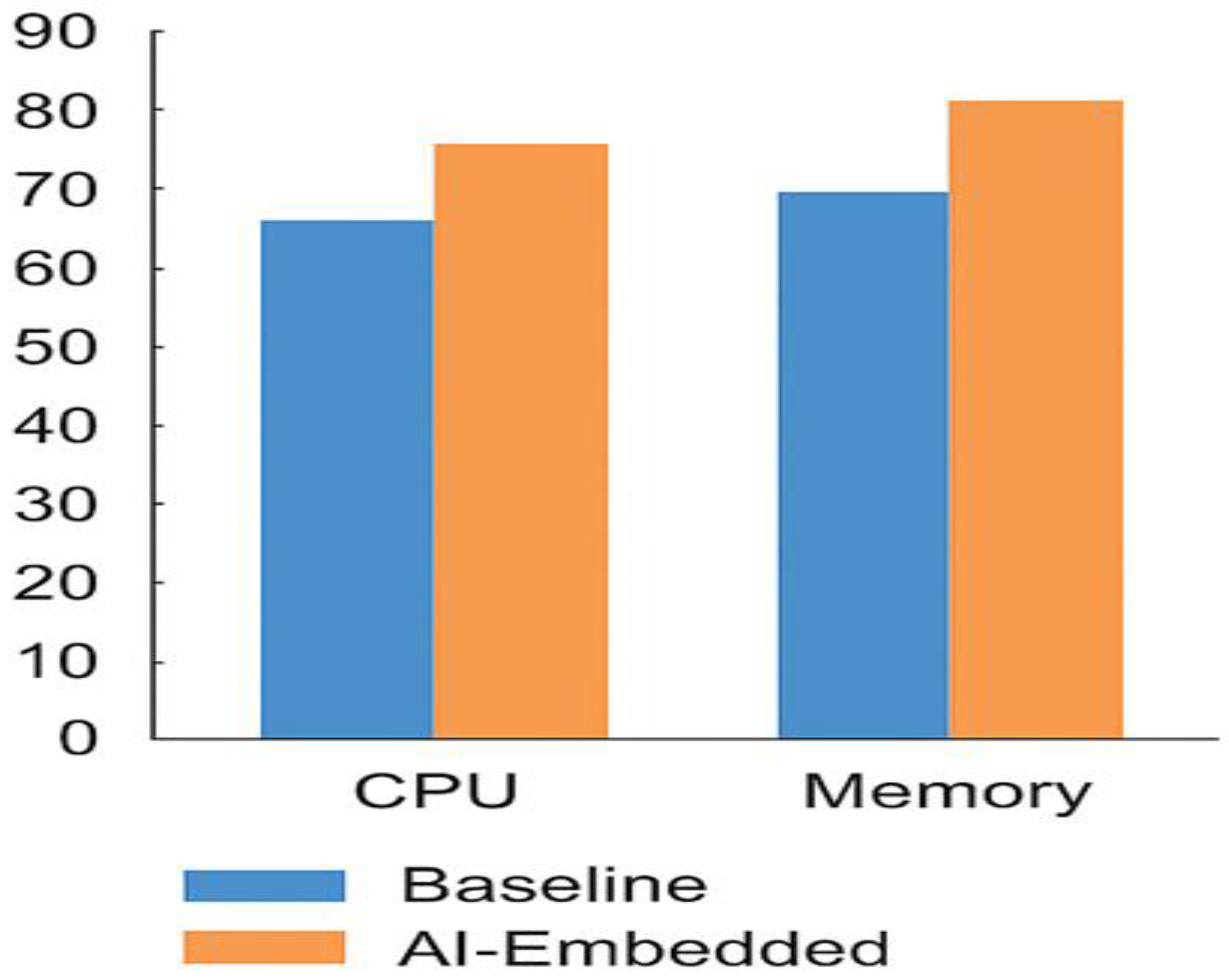
The system’s design, using intelligent technology within a network of servers, made better use of computing power during testing. The system typically used about 81% of its processing power, its memory, a jump from the 62% it used with the older method (
Table 1 and
Figure 2). The system works 19% better because it guesses what resources applications will need. It uses this information to move applications to the best servers before they even ask for more power. Assigning resources when needed cuts down on wasted capacity, guaranteeing that processing units work efficiently while tasks run. This system smartly spreads work among different virtual machines. It keeps everything running smoothly, avoiding overloaded servers or slowdowns.
Task Scheduling Efficiency
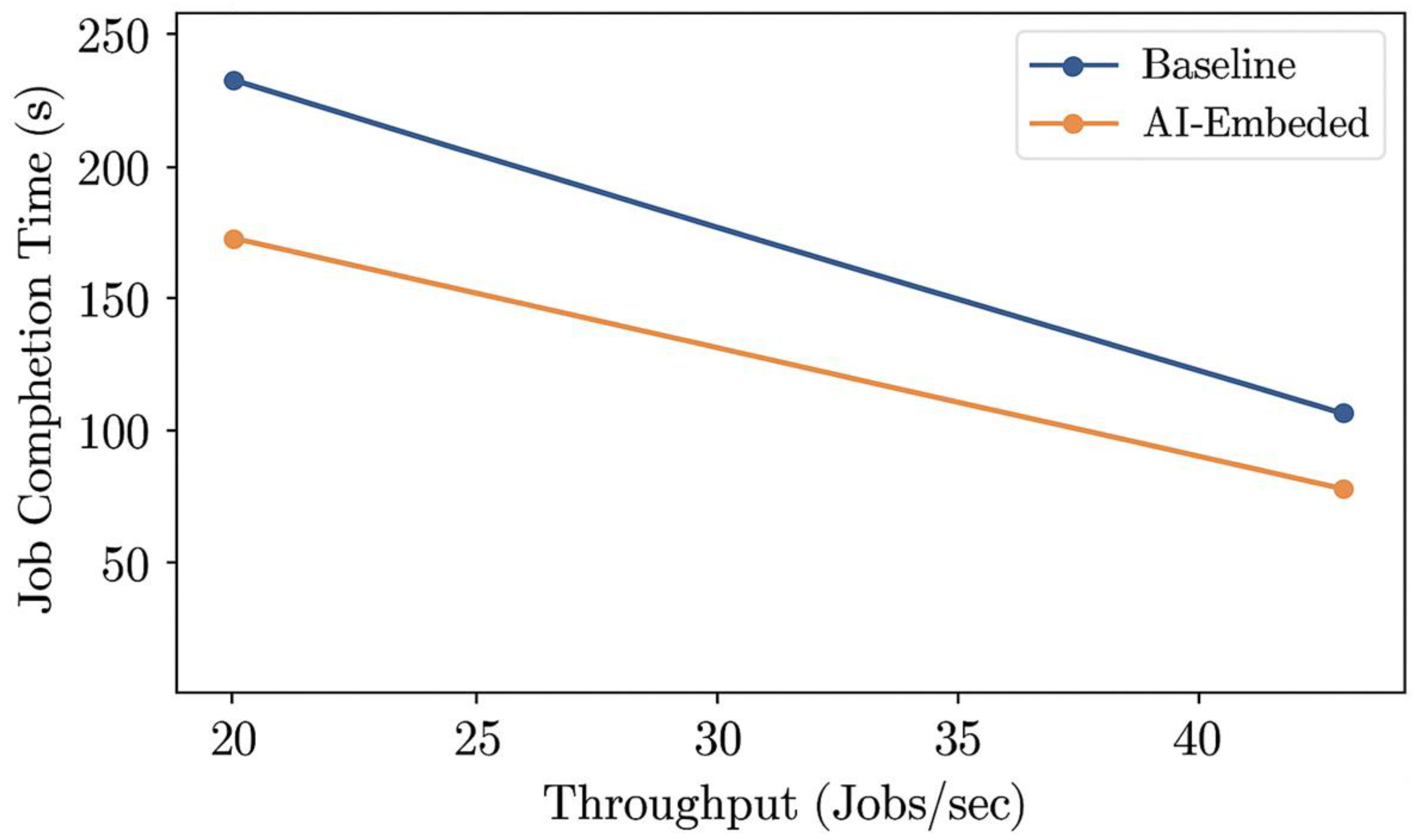
Combining clever scheduling techniques with artificial intelligence dramatically shortened how long tasks took to complete in the cloud. It typically took 182 seconds to finish a task initially, but a new system using artificial intelligence reduced that time to 141 seconds, a better result by 22.5 percent (
Table 2 and
Figure 3). The system works better because it uses smart learning techniques alongside other optimization methods, like swarm intelligence or operator-based approaches. These methods distribute jobs based on how much computing power is expected to be free, prioritizing important tasks. The system intelligently directs demanding tasks to the best available computer parts, like graphics cards or processors, so jobs start faster, resulting in quicker completion of work. The scheduling tool changes quickly when work gets busy. It constantly improves how tasks are assigned by observing, thinking, deciding, then doing.
Energy Efficiency
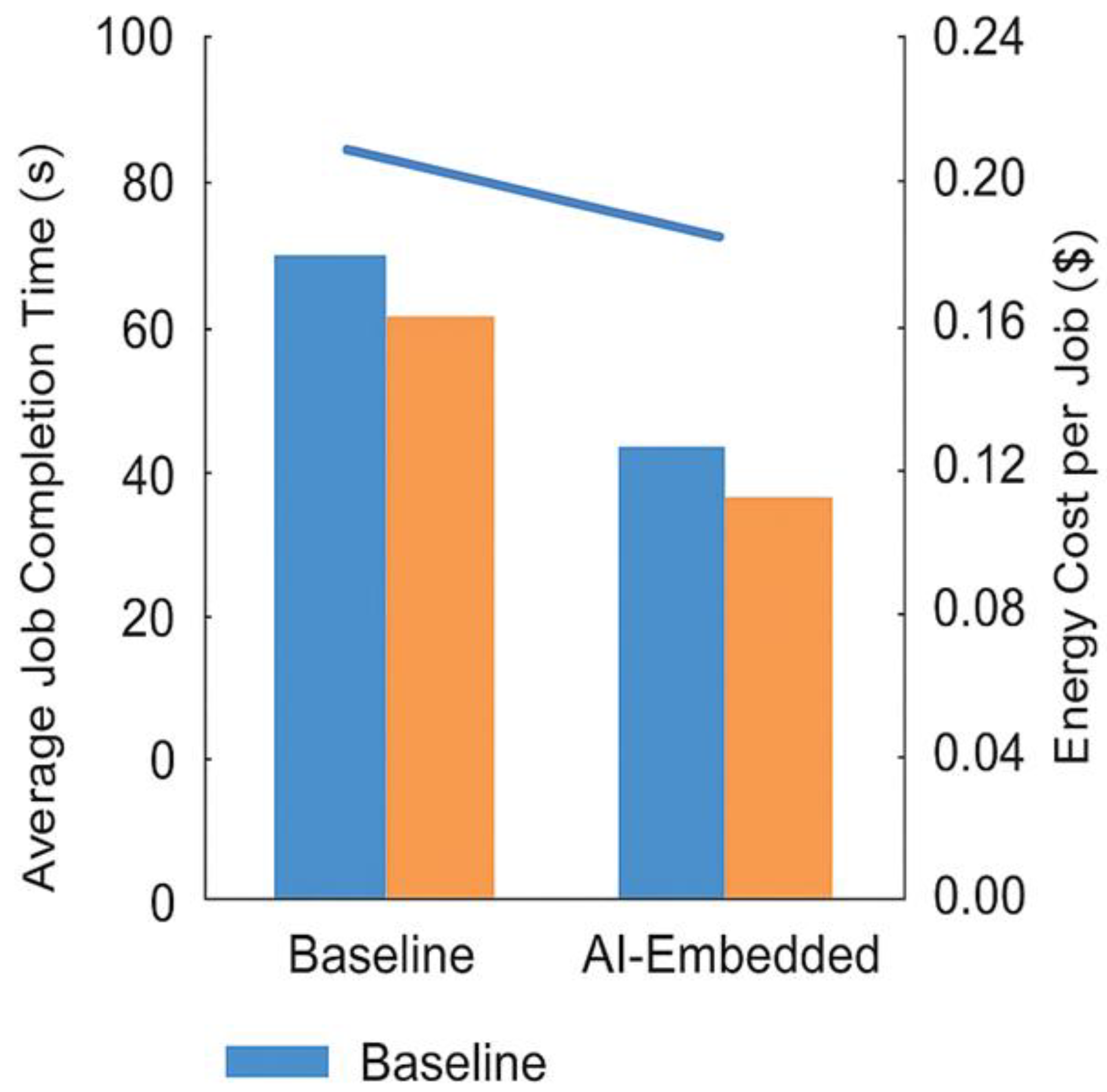
Taking care of the environment is really important when using cloud services today. Using smart controls, the system used 940 kilowatt-hours of energy. Without these controls, it would have used 1180 kilowatt-hours. This is a decrease of about 20 percent, a considerable saving (
Table 3 and
Figure 4). Using less power when setting up systems, also forecasting when more capacity will be needed, really helped lower costs. The system saves power by using virtual machines more efficiently, also it turns off servers when they aren't needed. This happens without affecting how well things work for users. The system considers how much power it uses when making choices. It aims for good results while also being environmentally responsible, rewarding efficiency.
Security Performance
The system found unusual activity, boosting cloud security. Using a team of autoencoders working together, with help from detection systems that create realistic scenarios, spotted intrusions 95.6% of the time. Traditional systems that look for known patterns only caught 87% of intrusions, a difference of 8.6%. The system spots tricky malware, detects unusual activity, learns what is typical, then checks information from various sources to find problems. This system keeps private information from each computer secure. It allows everyone to learn together without sharing details about each system. Security systems now use smart technology to change access rights instantly, looking at what’s happening right now. This limits opportunities for attacks, stopping people who shouldn’t get in from doing so.
5.4. Observations and Insights
A cloud system using artificial intelligence offers some clear benefits compared to older ways of managing cloud services
The system constantly adjusts to new tasks, lessening the need for set limits, or someone to step in manually. The system forecasts needs, adjusts resources automatically, then schedules tasks using smart technology. This way, computing power changes with use.
This system uses intelligent methods working together. It combines learning from rewards, predicting future needs, spotting unusual activity, to achieve several goals at once. These include saving resources, improving how tasks are organized, lowering energy use, strengthening security. This system looks at problems in a complete way, giving better results than older, simpler methods.
Using artificial intelligence improves how things work, yet it requires more processing power. To keep things working quickly, we need to watch how long it takes to train systems, also how long it takes them to give answers. Improving models, building simpler designs, learning bit by bit are all essential for growth when using systems with lots of data.
6. Conclusion
This work showed a cloud system that uses artificial intelligence to improve how things are used, how jobs are organized, how power is saved, also how data is kept safe in today’s cloud setups. This system uses techniques like learning from past patterns, spotting unusual activity, then finding the best ways to manage things. It learns to predict demands, notices when something is off, employs methods inspired by nature to improve performance. All this creates cloud operations that adjust automatically, work smarter, require less human involvement.
This system works with four parts: it observes, understands, chooses what to do, then does it. It constantly checks things, figures out what might happen, makes choices, performs jobs automatically. Testing with CloudSim 6.0, using information from actual large cloud data centers, showed noticeable gains. Computer processing, memory use climbed to about 81%, jobs finished 22.5% faster, power use lowered by 20%, while spotting security problems became 95.6% more accurate. Cloud systems using artificial intelligence work better, remain safer, benefit the environment more than older cloud setups.
The system adjusts easily to different tasks, changing needs, developing security problems. It grows with demand, remaining flexible. This system uses smart forecasting, efficient methods, automatic management, to build a base for future self-running cloud computing. We can improve this system by trying out learning from shared data, using multiple cooperating programs that learn through trial, error, connecting it to devices immediately for faster processing. These changes will build cloud systems that work everywhere, think for themselves.
References
- Kumar, T. V. (2017). Designing Resilient Multi-Tenant Applications Using Java Frameworks.
- Tambi, V. K. (2025). Multi-Cloud Data Synchronization Using Kafka Stream Processing. Available at SSRN 5366148.
- Tambi, V. K. (2025). Serverless Frameworks for Scalable Banking App Backends. Available at SSRN 5366139.
- Arora, A. (2025). Protecting Your Business Against Ransomware: A Comprehensive Cybersecurity Approach and Framework. Available at SSRN 5268155.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Tambi, V. K. (2022). Real-Time Compliance Monitoring in Banking Operations using AI. International Journal of Current Engineering and Scientific Research (IJCESR) Volume-9, Issue-9.
- Using Artificial Intelligence. Available at SSRN 5267988.
- Singh, B. (2025). Shifting Security Left Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Dalal, A. (2025). Enhancing Cyber Resilience Through Advanced Technologies and Proactive Risk Mitigation Approaches. Available at SSRN 5268078.
- Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Systems Administration, Deloitte Services LP (May 23, 2025).
- Dalal, A. (2025). Exploring Emerging Trends in Cloud Computing and Their Impact on Enterprise Innovation. Available at SSRN 5268114.
- Tambi, V. K. (2025). Cloud-Native Model Deployment for Financial Applications.
- Kumar, T. V. (2017). CROSS-PLATFORM MOBILE APPLICATION ARCHITECTURE FOR FINANCIAL SERVICES.
- Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Singh, H. (2025). The Impact of Advancements in Artificial Intelligence on Autonomous Vehicles and Modern Transportation Systems. Available at SSRN 5267884.
- Singh, H. (2025). Leveraging Cloud Security Audits for Identifying Gaps and Ensuring Compliance with Industry Regulations. Available at SSRN 5267898.
- Arora, A. Detecting and Mitigating Advanced Persistent Threats in Cybersecurity Systems.
- Arora, A. (2025). Challenges of Integrating Artificial Intelligence in Legacy Systems and Potential Solutions for Seamless Integration. Available at SSRN 5268176.
- Singh, H. (2025). Advanced Cybersecurity Techniques for Safeguarding Critical Infrastructure Against Modern Threats. Available at SSRN 5267496.
- Singh, B. Ensuring Data Integrity and Availability with Robust Database Security Protocols.
- Dalal, A. (2025). Building Comprehensive Cybersecurity Policies to Protect Sensitive Data in the Digital Era. Available at SSRN 5268080.
- Dalal, A. (2025). Designing Zero Trust Security Models to Protect Distributed Networks and Minimize Cyber Risks. Available at SSRN 5268092.
- Dalal, A. (2025). Implementing Robust Cybersecurity Strategies for Safeguarding Critical Infrastructure and Enterprise Networks. Available at SSRN 5268076.
- Dalal, A. (2025). Addressing Challenges in Cybersecurity Implementation Across Diverse Industrial and Organizational Sectors. Available at SSRN 5268082.
- Dalal, A. (2025). Harnessing the Power of SAP Applications to Optimize Enterprise Resource Planning and Business Analytics. Available at SSRN 5268096.
- Singh, B. Database Security Audits: Identifying and Fixing Vulnerabilities before Breaches.
- Singh, B. The Role of Artificial Intelligence in Modern Database Security and Protection.
- Singh, B. (2025). Automating Security Testing in CI/CD Pipelines using DevSecOps Tools a Comprehensive Study. CD Pipelines using DevSecOps Tools a Comprehensive Study (May 23, 2025).
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844.
- Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914.
- Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cybersecurity Risks in Supply Chains. Available at SSRN 5267866.
- Singh, B. CYBER SECURITY FOR DATABASES: ADVANCED STRATEGIES FOR THREAT DETECTION AND RESPONSE.
- Singh, B. (2025). Key Oracle Security Challenges and Effective Solutions for Ensuring Robust Database Protection. Available at SSRN 5267946.
- Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities.
- Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128.
- Dalal, A. (2025). Maximizing Business Value through Artificial Intelligence and Machine Learning in SAP Platforms. Available at SSRN 5268102.
- Arora, A. (2025). Building Responsible Artificial Intelligence Models That Comply with Ethical and Legal Standards. Available at SSRN 5268172.
- Arora, A. (2025). THE IMPACT OF GENERATIVE AI ON WORKFORCE PRODUCTIVITY AND CREATIVE PROBLEM SOLVING. Available at SSRN 5268208.
- Arora, A. (2025). Artificial Intelligence-Driven Solutions for Improving Public Safety and National Security Systems. Available at SSRN 5268174.
- Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204.
- Arora, A. (2025). Enhancing Customer Experience across Multiple Business Domains using Artificial Intelligence. Available at SSRN 5268178.
- Sidharth, S. (2016). The Role of AI in Automated Threat Hunting.
- Sidharth, S. (2016). The Role of Artificial Intelligence in Enhancing Automated Threat Hunting 1Mr. Sidharth Sharma.
- Sidharth, S. (2017). Cybersecurity Approaches for IoT Devices in Smart City Infrastructures.
- Sidharth, S. (2019). DATA LOSS PREVENTION (DLP) STRATEGIES IN CLOUD-HOSTED APPLICATIONS.
- Sidharth, S. (2017). Real-Time Malware Detection Using Machine Learning Algorithms.
- Sidharth, S. (2018). Optimized Cooling Solutions for Hybrid Electric Vehicle Powertrains.
- Singh, B. (2025). Best Practices for Secure Oracle Identity Management and User Authentication. Available at SSRN 5267949.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Dalal, A. (2025). Exploring Next-Generation Cybersecurity Tools for Advanced Threat Detection and Incident Response. Available at SSRN 5268086.
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Singh, H. Artificial Intelligence for Predictive Analytics Gaining Actionable Insights for Better Decision-Making.
- Dalal, A. (2025). Leveraging Artificial Intelligence to Improve Cybersecurity Defences Against Sophisticated Cyber Threats. Available at SSRN 5268084.
- Sidharth, S. (2015). AI-Driven Detection and Mitigation of Misinformation Spread in Generated Content.
- Sidharth, S. (2018). Post-Quantum Cryptography: Readying Security for the Quantum Computing Revolution.
- Sidharth, S. (2022). Zero Trust Architecture: A Key Component of Modern Cybersecurity Frameworks.
- Singh, H. (2025). Evaluating AI-Enabled Fraud Detection Systems for Protecting Businesses from Financial Losses and Scams. Available at SSRN 5267872.
- Singh, H. (2025). Building Secure Generative AI Models to Prevent Data Leakage and Ethical Misuse. Available at SSRN 5267908.
- Singh, H. (2025, May). The Importance of Cybersecurity Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. In Meeting Regulatory and Compliance Standards (May 23, 2025).
- Sidharth, S. (2016). Establishing Ethical and Accountability Frameworks for Responsible AI Systems.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).