Submitted:
01 September 2025
Posted:
02 September 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Contributions
- i.
- A novel blockchain-based authentication method for RPL.
- ii.
- A thorough evaluation of our proposed method using simulations.
- iii.
- We demonstrate that the proposed method can effectively mitigate routing attacks in IoT-LLNs.
- iv.
- Blockchain’s inherent immutability and transparency safeguard routing information from tampering and manipulation, preventing malicious nodes from disrupting network operations.
- v.
- Smart contracts automate the authentication process, reducing the overhead associated with manual verification and expediting the response to potential threats.
- vi.
- Blockchain’s distributed architecture can accommodate a growing number of nodes without compromising performance, making it suitable for large-scale IoT-LLNs.
1.2. Problem Statement
1.3. Related Work
2. Background
2.1. Routing Protocol for Low Power and Lossy Networks (RPL)
2.1.1. Blockchain Technology Overview
2.1.2. Security Considerations in IoT-LLNs
2.1.3. Addressing Security Vulnerabilities in RPL
2.2. Blockchain
2.3. Smart Contracts for Routing Attack Detection
2.4. Blockchain for Enhanced RPL Security
3. RPL Security in IoT Environment
3.1. Security Attacks on 6LowPAN and RPL Networks
3.1.1. Version Number Attack (VNA)
3.1.2. Decreased Rank Attack (DRA)
3.1.3. Increased Rank Attack (IRA)
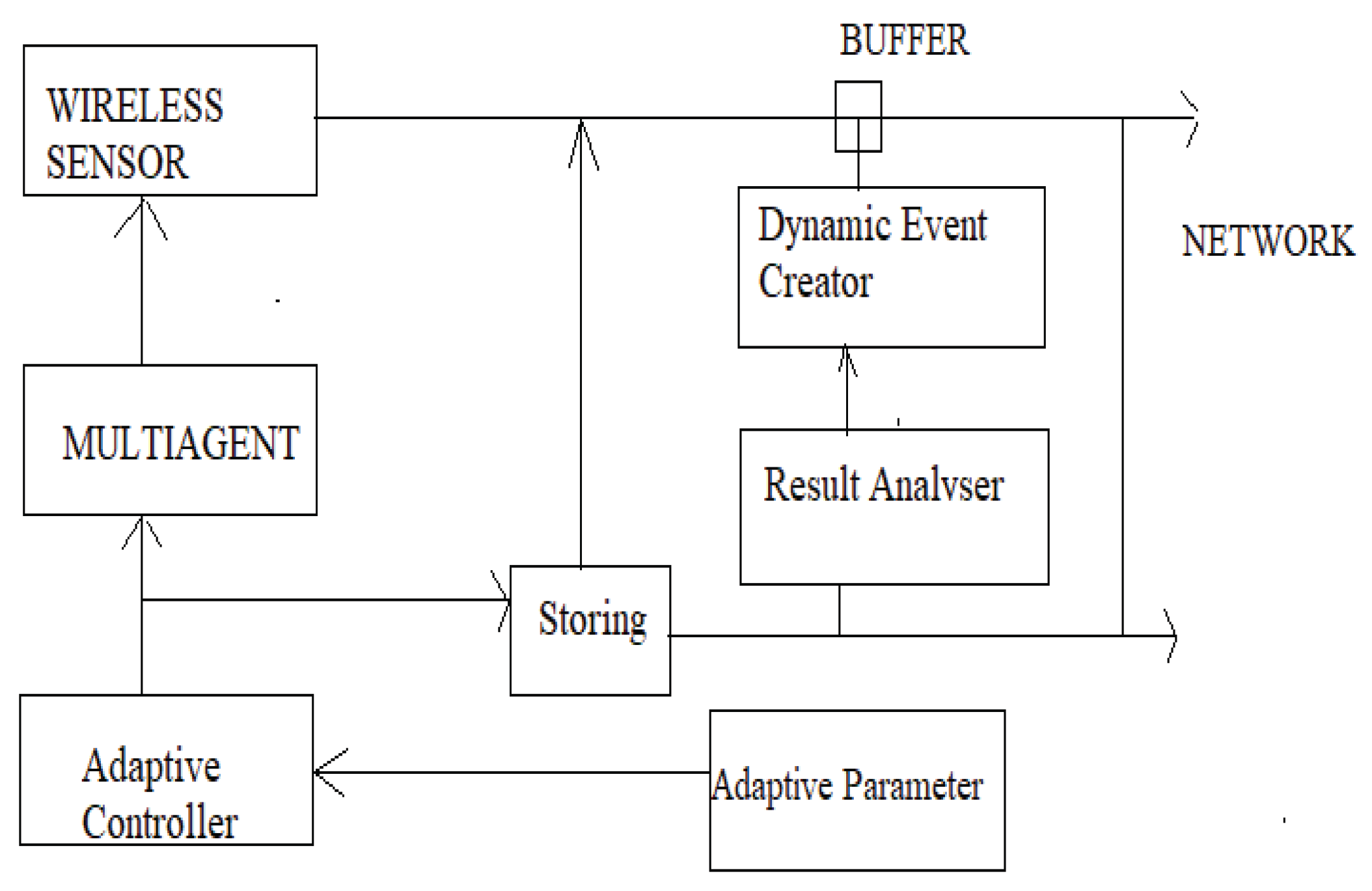
4. The Proposed IbiboRPL Chain Solution
4.1. Enhancing Security and Scalability with the IbiboRPLChain Solution
4.2. Optimising Performance with Balanced Distributed Variance Estimation
4.3. The Role of Multiagents in IoT Applications
4.4. Proposed Objective: Tracking Multiagents with Multiple Locations
4.5. System Model and Multiagent Control
4.6. Multiagent Leader and Consensus-Based Signal Points
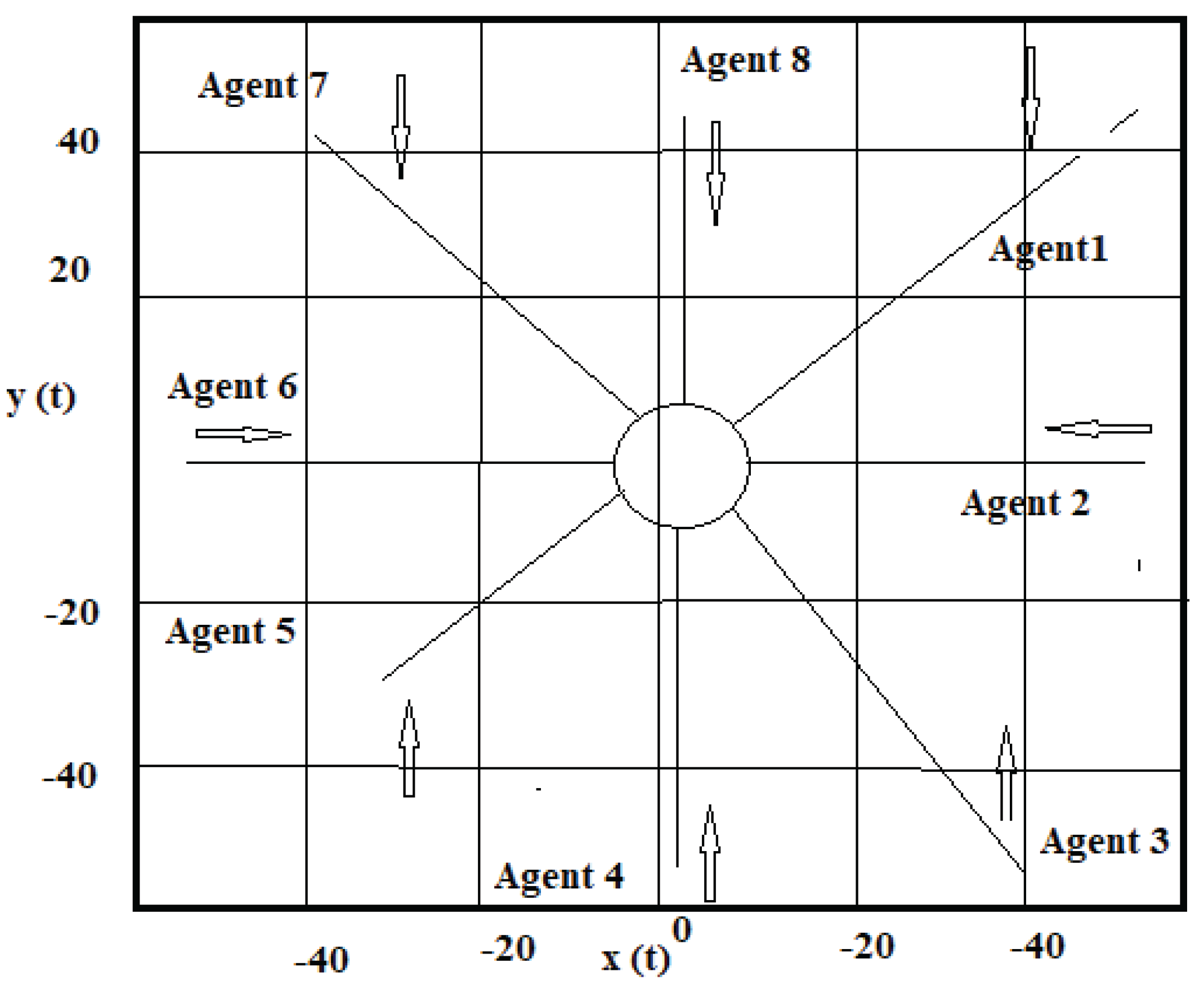
4.7. Experimental Simulation Scenarios
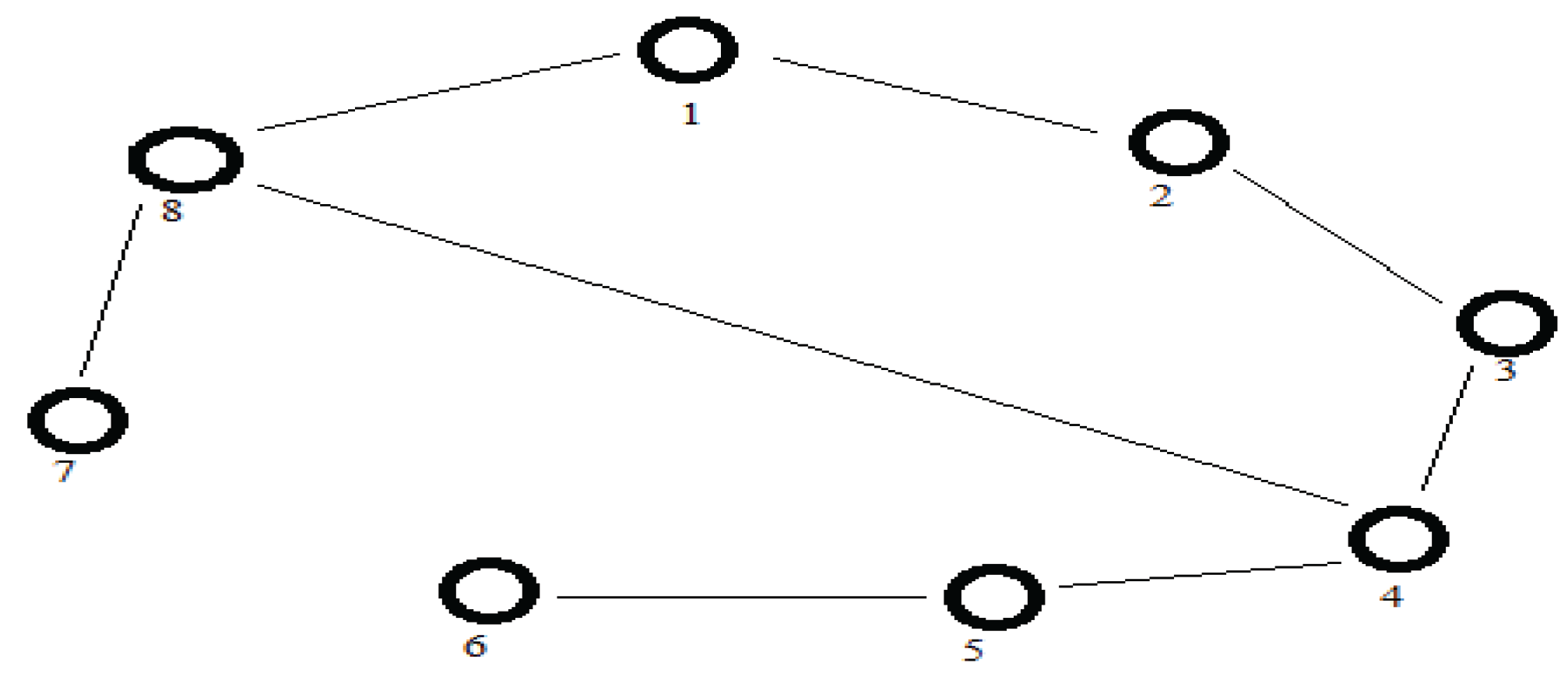
4.7.1. Example 1: Triggering Experiment
- and are the multiagent coordination points of different angles
- is the regular velocity of the respective nodes
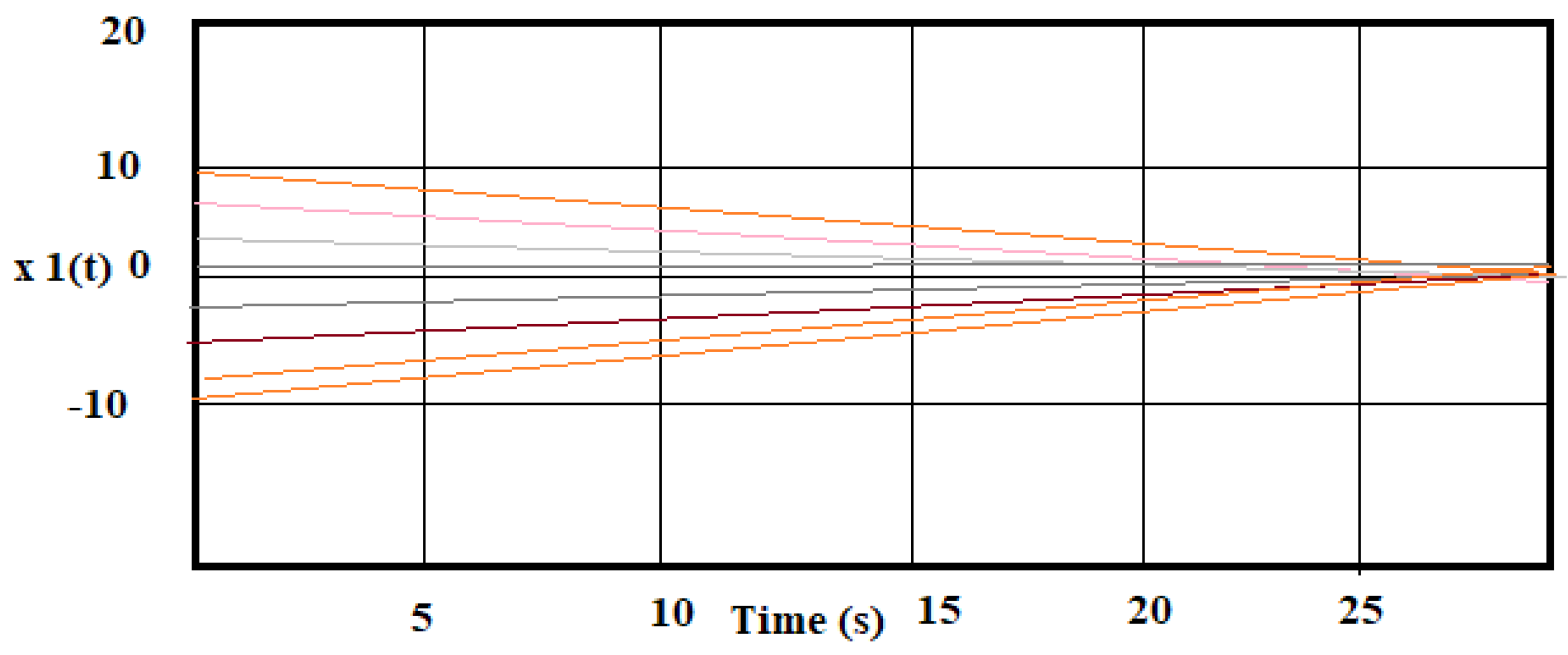
4.7.2. Example 2: Performance Evaluation
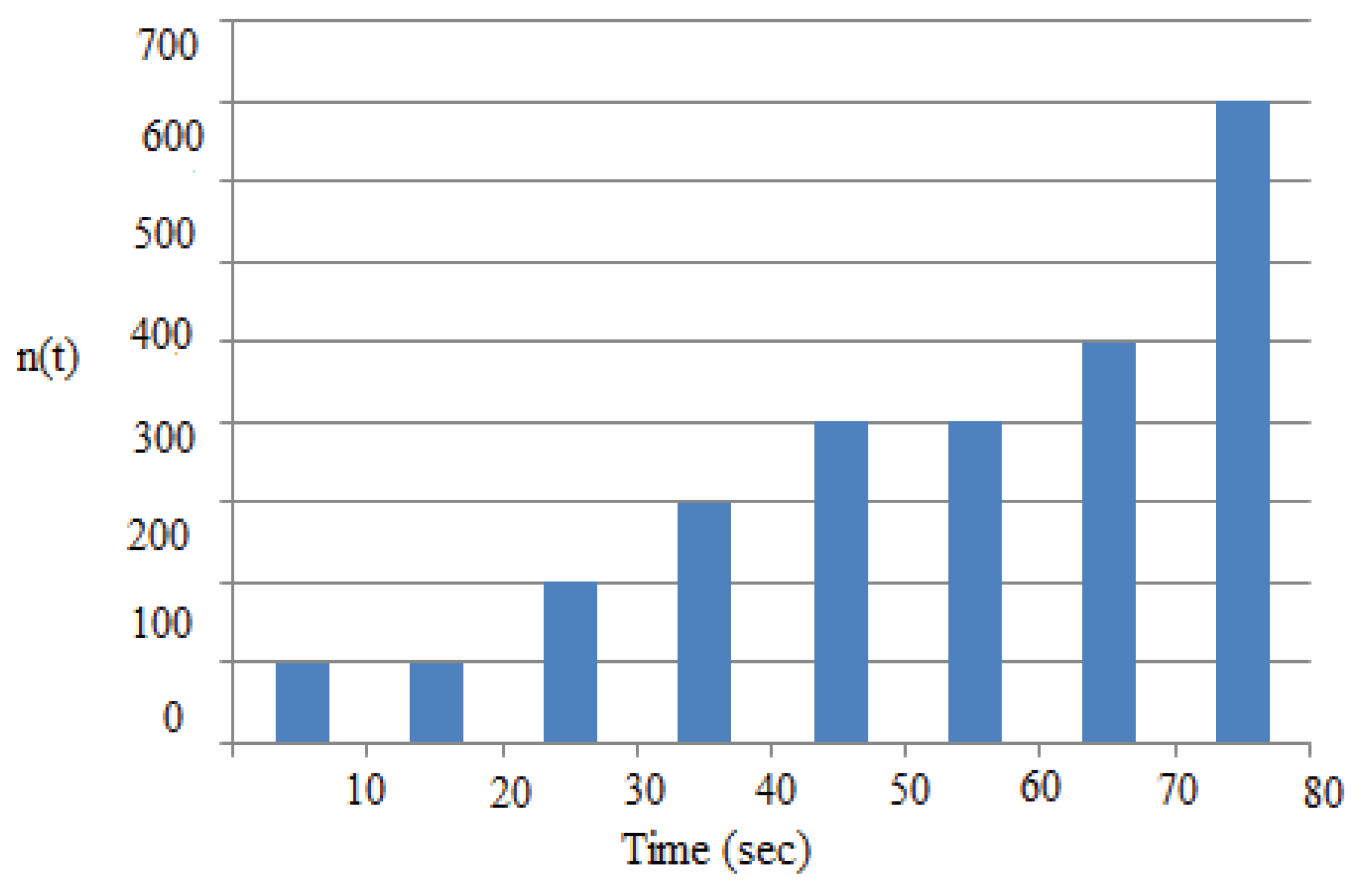
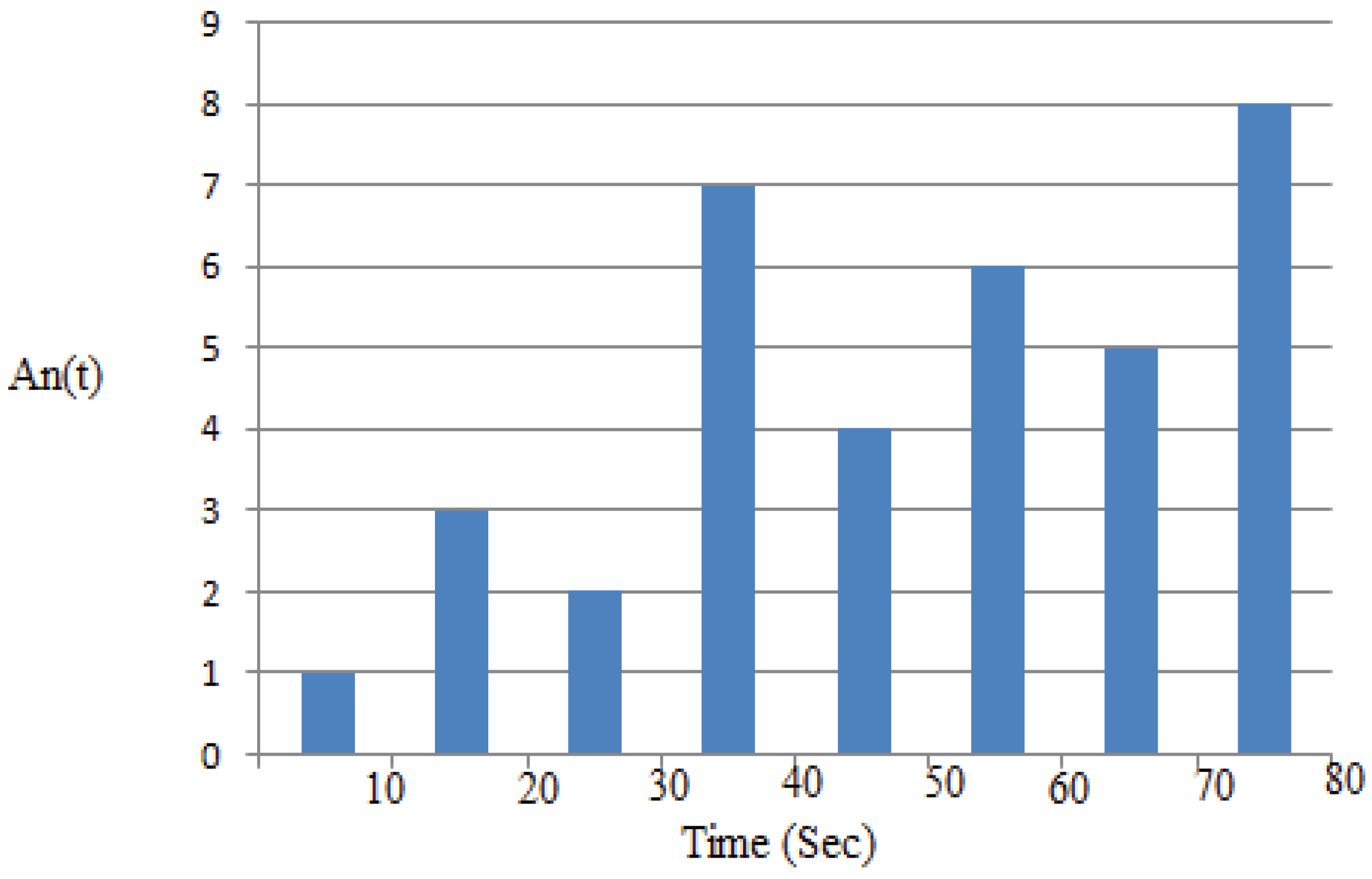
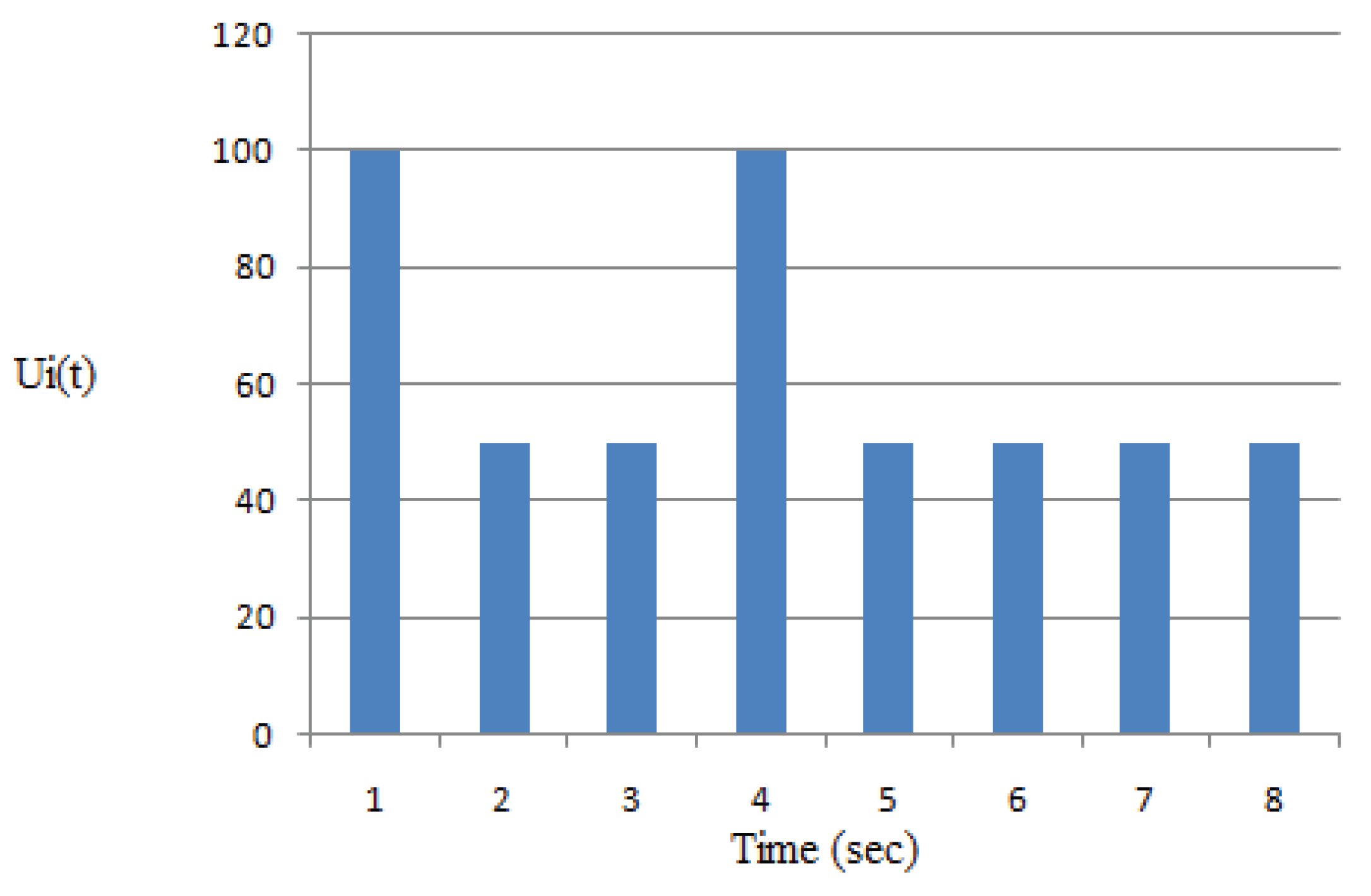
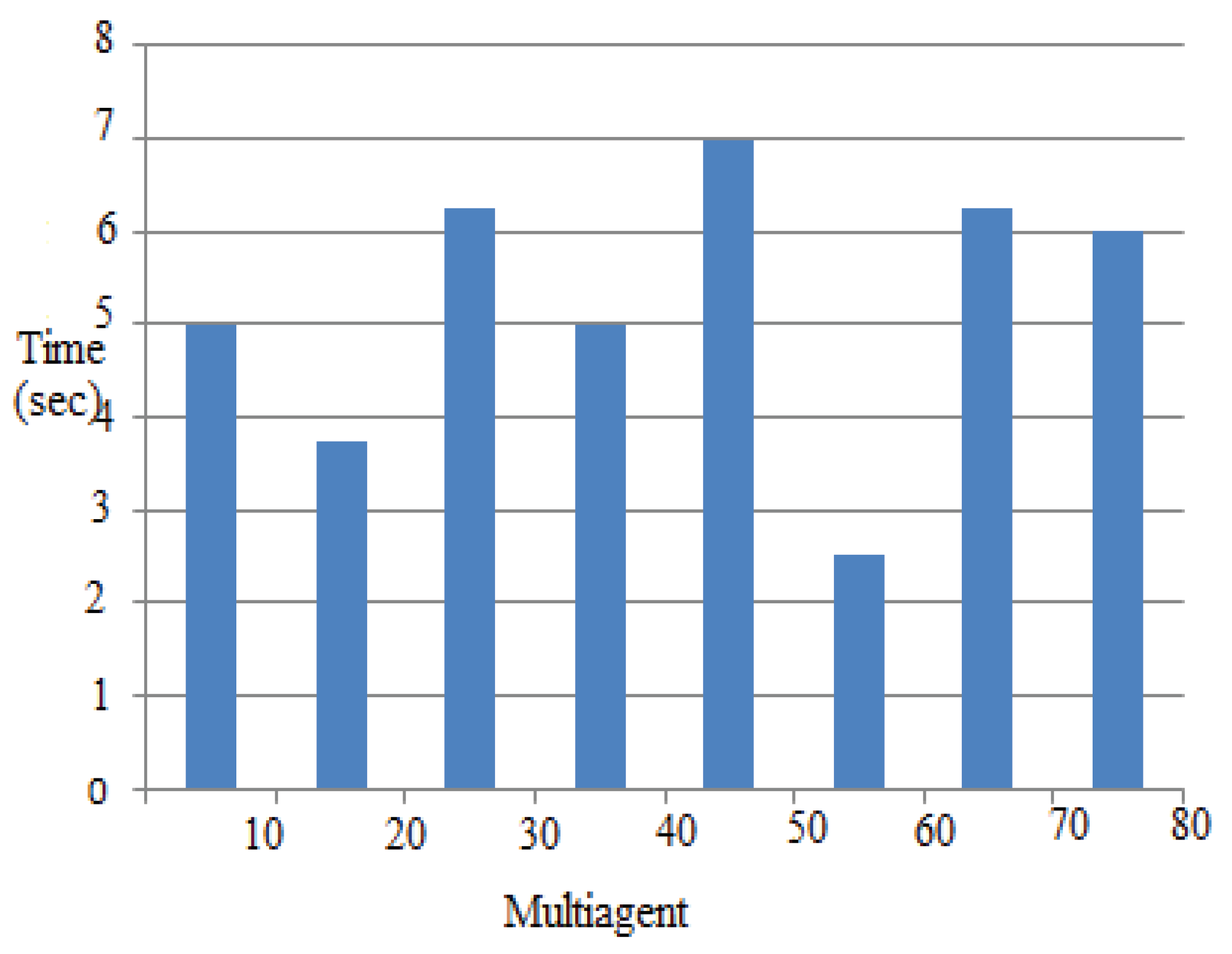
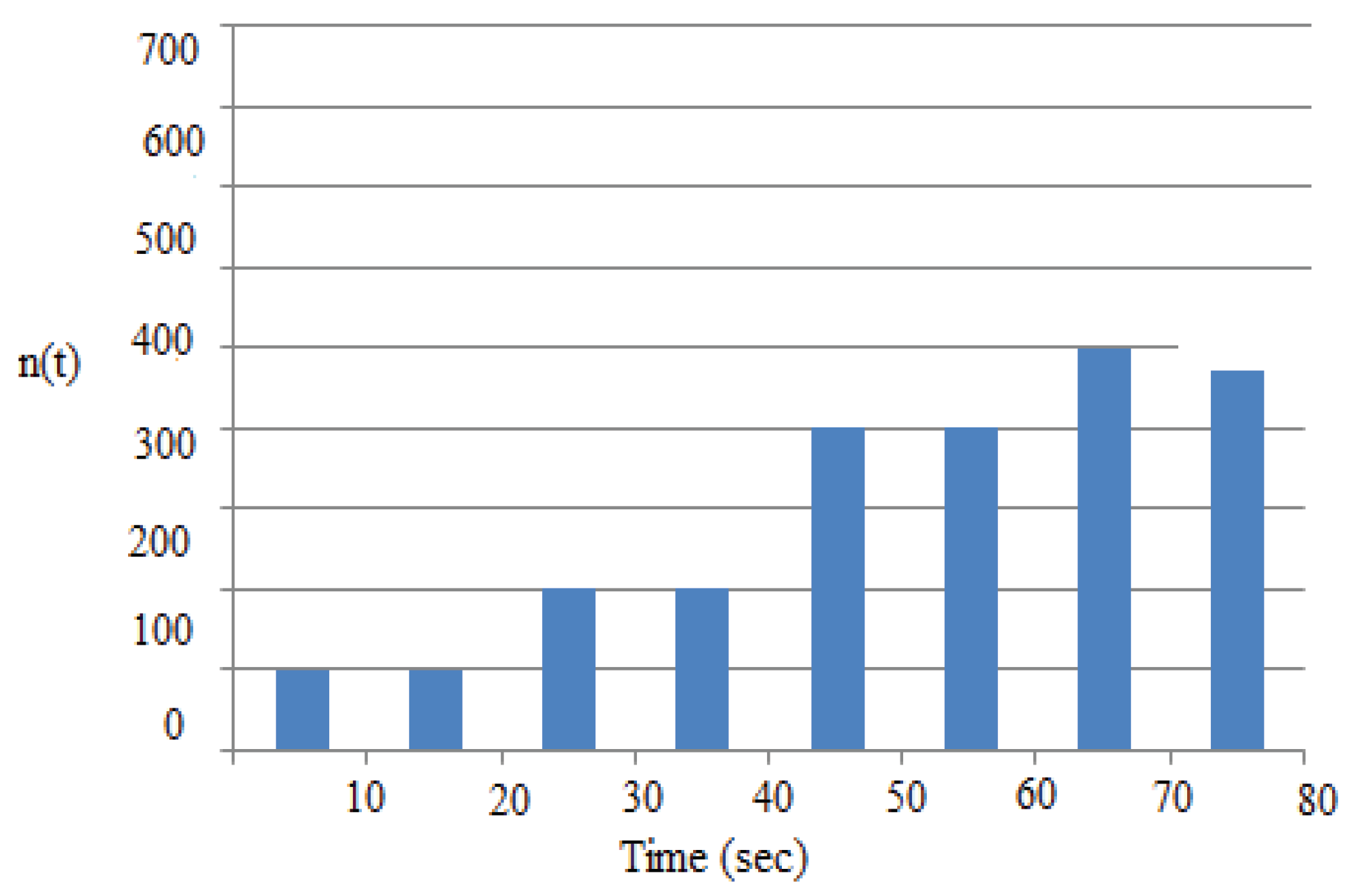
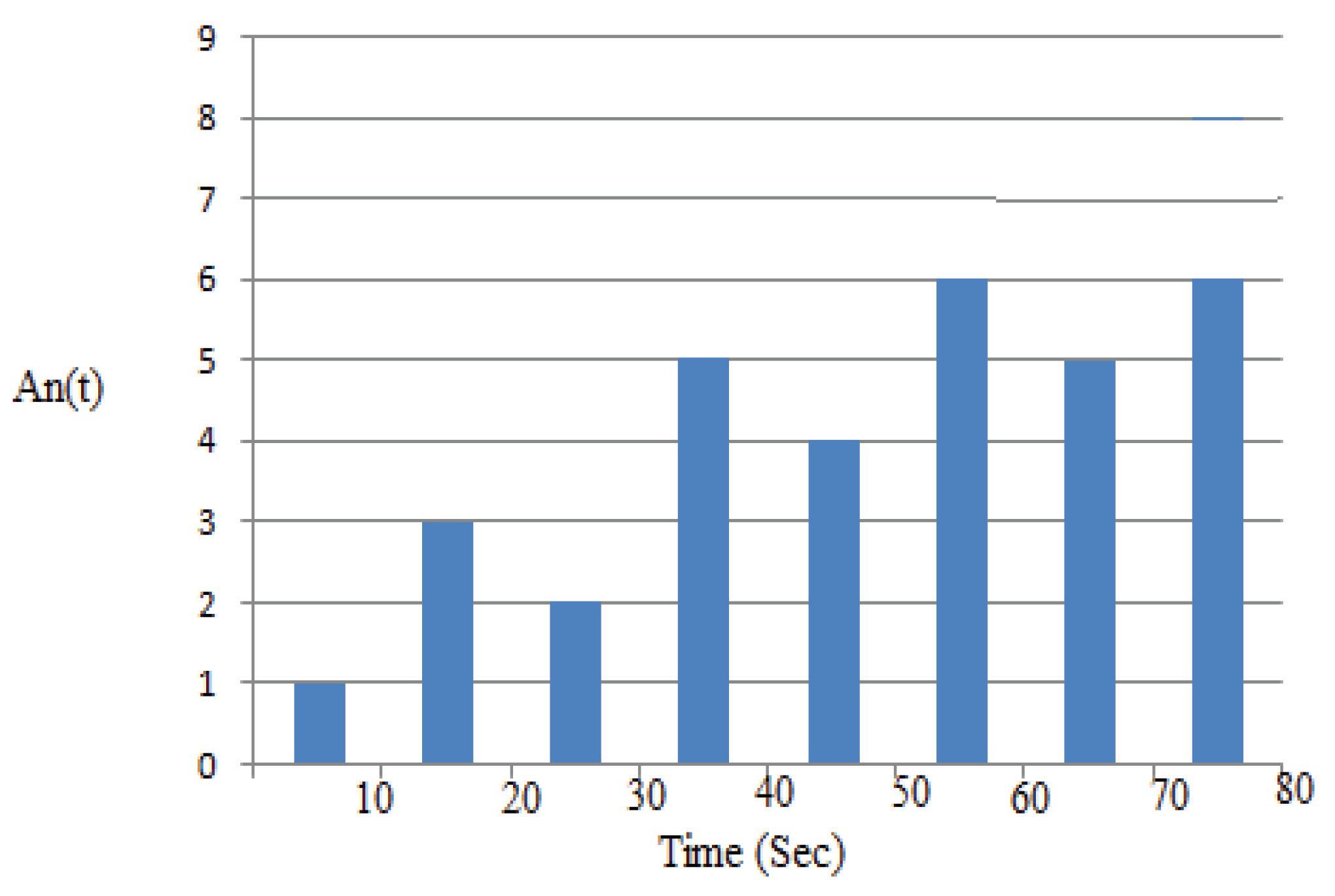
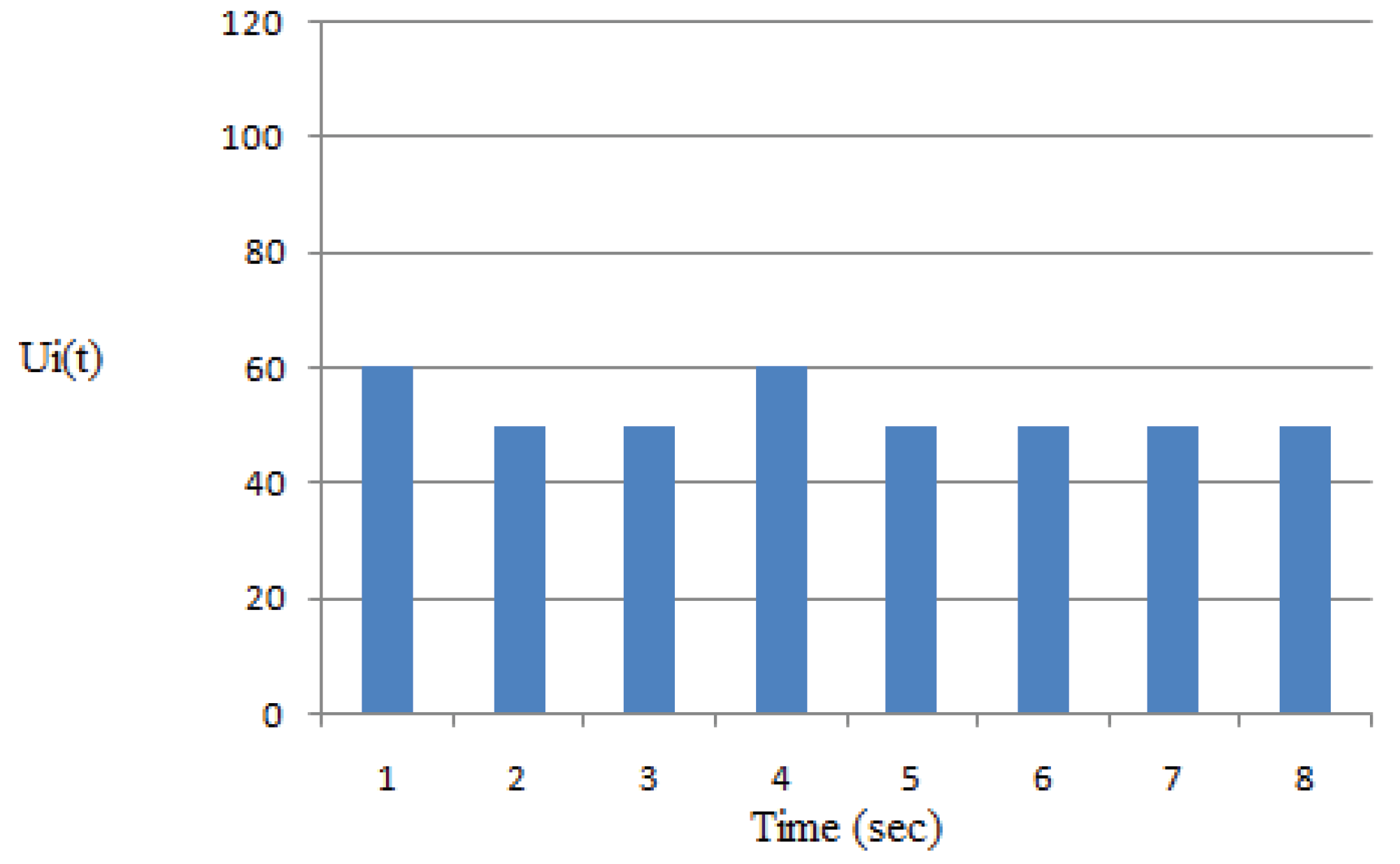
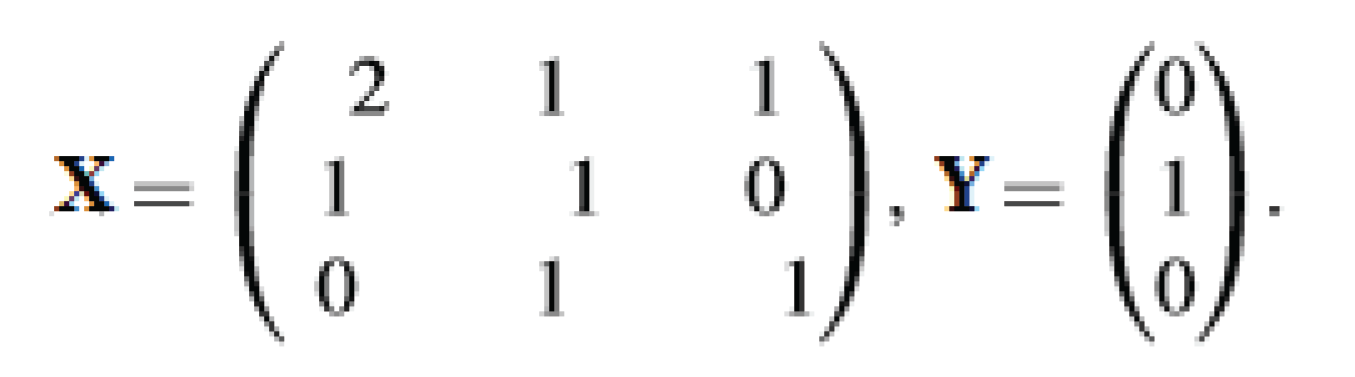

| Feature | Existing – Limited Agents and Specific Time Schedules | Proposed – IbiboRPLChain Solution System | Improvement |
| Methodology | Mac Protocol Based Scheduling Method | Blockchain based Authentication Method | Authentication System |
| Triggering instants | High (100) | Reduced by 50% (50) | Significant reduction |
| Time | Slow (100 seconds) | Improved by 2x (50 seconds) | Twice as fast |
| Consensus | Not achieved (0%) | Achieved (100%) | Significant improvement |
| Activeness | Low (10%) | Increased by 3x (30%) | Significant improvement |
| Security | Low (20%) | Improved by 4x (80%) | Significant improvement |
| Network computation time | High (100 seconds) | Reduced by 3x (33 seconds) | Significant reduction |
| Propagation | Unstable (0%) | Stabilised (100%) | Significant improvement |
| Time evolution strength | Low (10%) | Increased by 5x (50%) | Significant improvement |
| Feature | Existing Method –Decentralised Method | IbiboRPLChain Solution | Bitcoin | Ethereum | Hyperledger Fabric |
| Author Name | Konstantinos Tsoulias1 [8] | Our Solution | S. Lande [16] | R. Shang [23] | D. H. Nguyen [33] |
| Security | Uses SHA-256 to secure the blockchain. | Uses a combination of cryptographic algorithms to secure the blockchain, including SHA-256, ECDSA, and Merkle trees. | Uses SHA-256 to secure the blockchain. | Uses SHA-256 to secure the blockchain. | Uses PBFT to secure the blockchain. |
| Triggering instants | Transactions | Events or transactions | Block completion | Transactions | Transactions |
| Time | Transaction Time | Block time | Block time | Transaction time | Transaction time |
| Consensus | Proof of Work (PoW) | Proof of Work (PoW) | Proof of Work (PoW) | Proof of Stake (PoS) | Byzantine Fault Tolerance (BFT) |
| Propagation | Sharding | Gossip protocol | Gossip protocol | Sharding | Gossip protocol |
| Time evolution strength | Strong | Strong | Strong | Strong | Strong |
| Activeness | Active | Passive | Passive | Passive | Active |
| Advantages | Secure, widely adopted | Secure, scalable, efficient | Secure, widely adopted | Secure, supports smart contracts | Secure, enterprise-grade |
| Adaptability | Limited adaptability | Can be adapted to a variety of IoT-LLN environments | Limited adaptability | Limited adaptability | Limited adaptability |
| Computational Cost | Moderate computational cost | Low computational cost | High computational cost | High computational cost | Moderate computational cost |
| Features | Supports smart contracts. | Supports secure authentication, data integrity, and non-repudiation. | Supports secure payments. | Supports smart contracts. | Supports enterprise-grade security. |
5. Analysis and Discussions
- Identity Authentication Each application has an enormous number of users, because of that; it is required to apply the privilege and deny illegal access by employing the authentication mechanism.
- Data Storage and Recovery The data transmission among different wireless objects and applications exposed to many security threats. This state needs the data integrity and privacy to protect the transmitted data from exploitation.
- Handling huge data the application layer is processing a large amount of data, which leads to data loss during the transmission process. This problem may affect the efficiency of the wireless processes.
- The Software Vulnerabilities the programming errors in application software lead to offer the security exploitation.
- Confidentiality is equivalent to privacy; it assures that the data is protected and only accessible to authorised users.
- Integrity Data integrity is a security requirement to ensure the accuracy, completeness, and consistency of the data.
- Availability of data refers to assuring that authorised users can access the information and services whenever they need it.
- Access control Access control is a security procedure used to control who or what can view or utilise resources and manage server communication.
- Authentication is the process of recognising a user’s identity before launching a communication channel between two parties.
- Authorisation defines the rights and privileges of the authentication party after gaining access to a system.
6. Conclusion
References
- HAN LIU1, DEZHI HAN1, DUN LI.1 , “Fabric-iot: a Blockchain Based Access Control System in IoT” 10.1109/ACCESS.2020.2968492, IEEE Access., VOLUME 4, 2016.
- Imran makhdoom , Farzad Tofigh , Ian Zhou ., “PLEDGE: A Proof-of-Honesty based Consensus Protocol for Blockchain-based IoT Systems “IEEE 978-1-7281-6680- September 03 2020.
- Bayan HazaaAIDoaies ,Dr.Hayaalmagwashi ,” Exploitation of the Promising Technology: Using BlockChain to Enhance the Security of IoT” 978-1-5386-4110-1,IEEE -2018.
- Wassim M. Haddad, Tanmay Rajpurohit, and Xu Jin ., “Stochastic Semistability for Nonlinear Dynamical Systems with Application to Consensus on Networks with Communication Uncertainty”0018-9286 ., IEEE – 2019.
- Stefanos Leonardos ,DaniëlReijsbergen, and Georgios Piliouras., “PREStO: A Systematic Framework for Blockchain Consensus Protocols” Digital Object Identifier 10.1109/TEM.2020.2981286.
- W.Liang, M.Tang*,Member,IEEE,J.Long,X.Peng,J.XuandK.C.Li., “ASecureFabricBlockchain-basedDataTransmissionTechniqueforIndustrialInternet-of-Things”1551-3203 IEEE- 2018.
- Chao Qiu, ,Haipeng Yao, , F. Richard Yu, , Chunxiao Jiang, , and Song Guo, “A Service-Oriented Permissioned Blockchain for the Internet of Things”1939-1374 IEEE- 2019.
- Konstantinos Tsoulias1, Georgios Palaiokrassas1, Georgios Fragkos2, Antonios Litke1 and Theodora Varvarigou1., “A graph model based blockchain implementation for increasing performance and security in decentralized ledger systems” 10.1109/ACCESS.2020.3006383.
- Wattana Viriyasitavat, Li Da Xu, Zhuming Bi, DanupolHoonsopon, and NuttirudeeCharoenruk,” Managing QoS of Internet-of-Things Services Using Blockchain” Digital Object Identifier 10.1109/TCSS.2919667, 2019.
- Jun Wu, Mianxiong Dong, Kaoru Ota, Jianhua Li, and Wu Yang., “Application-Aware Consensus Management for Software-Defined Intelligent Blockchain in IoT” UTC from IEEE Xplore- May 03,2020.
- Wenjing Xiao, Chen Liu, Haoquan Wang, Ming Zhou, M. Shamim Hossain, Mubarak Alrashoud, Ghulam Muhammad.,” Blockchain for Secure-GaS: Blockchain-powered Secure Natural Gas IoT System with AI-enabled Gas Prediction and Transaction in Smart City” 2327-4662 IEEE- 2020.
- Lantao Xing, Qianwen Xu, Changyun Wen, Yu-Chu Tian∗, Yateendra Mishra, Gerard Ledwich, and Yongduan Song,”Robust Event-triggered Dynamic Average Consensus against Communication Link Failures with Application to Battery Control”IEEE - 2325-5870 ,2020.
- XiuYou , Changchun Hua , and Xinping Guan., “Self-Triggered Leader-Following Consensus for High-Order Nonlinear Multiagent Systems via Dynamic Output Feedback Control”Digital Object Identifier 10.1109/TCYB,2813423,2018.
- Xiangxiang Zeng, Wen Wang, Cong Chen, and Gary G. Yen.,”A Consensus Community-Based Particle Swarm Optimization for Dynamic Community Detection”Digital Object Identifier 10.1109/TCYB. 2938895, 2019.
- S. Bano et al., “SoK: Consensus in the age of blockchains,” in Proc. 1st ACMConf.Adv.FinancialTechnol.,Zurich,Switzerland,2019,pp.183– 198. [CrossRef]
- M. Bartoletti, S. Lande, and A. S. Podda, “A proof-of-stake protocol for consensus on bitcoin subchains,” in Financial Cryptography and Data Security, M. Brenner et al., Eds. Cham, Switzerland: Springer, 2017, pp. 568–584.
- B. Biais, C. Bisière, M. Bouvard, and C. Casamatta, “The blockchain folk theorem,” Institutd’ÉconomieIndustrielle, Toulouse, France, IDEI Working Papers 873, May 2017.
- J. Bonneau, “Hostile blockchain takeovers (short paper),” in Proc. 5th IFCA Workshop Bitcoin Blockchain Res., 2018, pp. 92–100.
- J. Brown-Cohen, A. Narayanan, C.-A. Psomas, and S. M. Weinberg, “Formal barriers to longest-chain proof-of-stake protocols,” in Proc. ACM Conf. Econ. Comput., 2019, pp. 459–473.
- L. Brünjes, A. Kiayias, E. Koutsoupias, and A.-P. Stouka, “Reward sharing schemes for stake pools,” 2018, arXiv:1807.11218.
- Ibibo, J.T. (2024). IoT Attacks Countermeasures: Systematic Review and Future Research Direction. In: Tan, Z., Wu, Y., Xu, M. (eds) Big Data Technologies and Applications. BDTA 2023. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 555. Springer, Cham. [CrossRef]
- R. Shang, H. Liu, L. Jiao, and A. M. Esfahani, “Community mining using three closely joint techniques based on community mutual membership and refinement strategy,” Appl. Soft Comput., vol. 61, pp. 1060–1073, Dec. 2017.
- R. Shang, W. Zhang, L. Jiao, R. Stolkin, and Y. Xue, “A community integration strategy based on an improved modularity density increment for large-scale networks,” Physica A Stat. Mech. Appl., vol. 469, pp. 471–485, Mar. 2017.
- J. T. Ibibo, “Emerging Challenges and Solutions in RPL Protocol: Research Review,” 2023 IEEE 28th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Edinburgh, United Kingdom, 2023, pp. 283-289. keywords: {Technological innovation;Reviews;Scalability;Machine learning;Linear programming;Energy efficiency;Routing protocols;RPL protocol;IoT networks;Routing protocol;Security vulnerabilities}. [CrossRef]
- X. Ma and D. Dong, “Evolutionary nonnegative matrix factorization algorithms for community detection in dynamic networks,” IEEE Trans. Knowl. Data Eng., vol. 29, no. 5, pp. 1045–1058, May 2017.
- Z. Meng, T. Yang, G. Li, W. Ren, and D. Wu, “Synchronization of coupled dynamical systems: Tolerance to weak connectivity and arbitrarily bounded time-varying delays,” IEEE Transactions on Automatic Control, vol. 63, no. 6, pp. 1791–1797, 2018.
- B. Wang, J. Wang, B. Zhang, W. Chen, and Z. Zhang, “Leader-follower consensus of multi-vehicle wirelessly networked uncertain systems subject to nonlinear dynamics and actuator fault,” IEEE Transactions on Automation Science and Engineering, vol. 15, no. 2, pp. 492–505, 2018. [2] Y. Zhao, Y. Liu, G. Wen, and G. Chen, “Distributed optimization of linear multi-agent systems: Edge-and node-based adaptive designs,” IEEE Transactions on Automatic Control, vol. 62, no. 7, pp. 3602–3609, 2017. [3] Y.-J. Liu and S. Tong, “Barrier lyapunov functions for nussbaum gain adaptive control of full state constrained nonlinear systems,” Automatica, vol. 76, pp. 143–152, 2017.
- S.-L. Du, X.-M. Sun, M. Cao, and W. Wang, “Pursuing an evader through cooperative relaying in multi-agent surveillance networks,” Automatica, vol. 83, pp. 155–161, Sep. 2017.
- W. He, C. Xu, Q.-L. Han, F. Qian, and Z. Lang, “L2 leader–follower consensus of networked Euler–Lagrange systems with external disturbances,” IEEE Trans. Syst., Man, Cybern., Syst., vol. 48, no. 11, pp. 1920–1928, Nov. 2018.
- V. N. Coelho, M. W. Cohen, I. M. Coelho, N. Liu, and F. G. Guimarães, “Multi-agent systems applied for energy systems integration: State-ofthe-art applications and trends in microgrids,” Appl. Energy, vol. 187, pp. 820–832, Feb. 2017.
- X. Ge and Q.-L. Han, “Distributed formation control of networked multi-agent systems using a dynamic event-triggered communication mechanism,” IEEE Trans. Ind. Elect 2017.
- W. He, G. Chen, Q.-L. Han, and F. Qian, “Network-based leaderfollowing consensus of nonlinear multi-agent systems via distributed impulsive control,” Inf. Sci., vol. 380, pp. 145–158, Feb. 2017.
- D. H. Nguyen, T. Narikiyo, and M. Kawanishi, “Robust consensus analysis and design under relative state constraints or uncertainties,” IEEE Trans. Autom. Control, vol. 63, no. 6, pp. 1784–1790, Jun. 2018.
- J. Yu and Y. Shi, “Scaled group consensus in multiagent systems with first/second-order continuous dynamics,” IEEE Trans. Cybern., vol. 48, no. 8, pp. 2259–2271, Aug. 2018.
- M. Zhao, C. Peng, W. He, and Y. Song, “Event-triggered communication for leader-following consensus of second-order multiagent systems,” IEEE Trans. Cybern., vol. 48, no. 6, pp. 1888–1897, Jun. 2018.
- X. Ge, Q.-L. Han, and X.-M. Zhang, “Achieving cluster formation of multi-agent systems under aperiodic sampling and communication delays,” IEEE Trans. Ind. Electron., vol. 65, no. 4, pp. 3417–3426, Apr. 2018.
- F. Li, K. Shaung, and S. Su. Q-Peer: A Decentralized QoS Registry Architecture for Web Services. Accessed: Apr. 8, 2019. [Online]. Available: https://link.springer.com/chapter/10.1007/978-3-540-74974-5_12.
- I. Haq, R. Alnemr, A. Paschke, E. Schikuta, H. Boley, and C. Meinel. Distributed Trust Management for Validating SLA Choreographies. Accessed: Apr. 8, 2019. [Online]. Available: https://pdfs. semanticscholar.org/63d5/d7c90287b423534ea3d28d15fb6a8a0a5e55. Pdf.
- NxT–The Blockchain Application Platform. Accessed: Apr. 8, 2019. [Online]. Available: https://nxtplatform.org/.
- Y. Lu, “Blockchain and the related issues: A review of current research topics,” J. Manage. Anal., vol. 5, no. 4, pp. 231–255, 2018.
- Y. Lu, “Blockchain: A survey on functions, applications and open issues,” J. Ind. Integr. Manage., vol. 3, no. 4, 2018, Art. no. 1850015.
- H. F. Atlam, A. Alenezi, M. O. Alassafi, and G. B. Wills, “Blockchain with Internet of Things: Benefits, challenges, and future directions,” Int. J. Intell. Syst. Appl., vol. 10, no. 6, pp. 40–48, 2018.
- M. H. Miraz and M. Ali, “Applications of blockchain technology beyond cryptocurrency,” 2018, arXiv:1801.03528. [Online]. Available: https://arxiv.org/abs/1801.03528.
- S. Madumidha, P. SivaRanjani, S. Rajesh, and S. Sivajumar, “Blockchain security for Internet of Things: A literature survey,” Int. J. Pure Appl. Math., vol. 119, no. 16, pp. 3677–3686, 2018.
- Ibibo, J.T. (2024). A Bibliometric Analysis and Comprehensive Overview of Security Attacks Against RPL in IoT Networks. In: Tran, K.P., Li, S., Heuchenne, C., Truong, T.H. (eds) The Seventh International Conference on Safety and Security with IoT. SaSeIoT 2023. EAI/Springer Innovations in Communication and Computing. Springer, Cham. [CrossRef]
- C. Du, X. Liu, W. Ren, P. Lu, and H. Liu, “Finite-time consensus for linear multi-agent systems via event-triggered strategy without continuous communication,? IEEE Trans. Control Netw. Syst. 2019 . [CrossRef]
- Ibibo, J.T., Japheth, B.R. (2024). RPL Protocol Using Contiki Operating Systems: A Review. In: Tran, K.P., Li, S., Heuchenne, C., Truong, T.H. (eds) The Seventh International Conference on Safety and Security with IoT. SaSeIoT 2023. EAI/Springer Innovations in Communication and Computing. Springer, Cham. [CrossRef]
- T. Liu and Z.-P. Jiang, “Event-based control of nonlinear systems with partial state and output feedback,” Automatica, vol. 53, pp. 10–22, 2015.
- L. Xing, C. Wen, Z. Liu, H. Su, and J. Cai, “Event-triggered output feedback control for a class of uncertain nonlinear systems,” IEEE Trans. Autom. Control, vol. 64, no. 1, pp. 290–297, 2018.
- X. Wang and M. D. Lemmon, “Event-triggering in distributed networked control systems,” IEEE Trans. Autom. Control, vol. 56, no. 3, pp. 586– 601, 2011.
- C. Nowzari, E. Garcia and J. Cort’ es, “Event-triggered communication andcontrolofnetworkedsystemsformulti-agentconsensus”,Automatica, vol. 105, pp. 1–27, 2019.
- J. George, X. Yi and T. Yang, “ Distributed robust dynamic average consensus with dynamic event-triggered communication,” IEEE Conference on Decision and Control (CDC), pp. 434–439, 2018.
- C. Li, E. A. A. Coelho, T. Dragicevic, J. M. Guerrero, and J. C. Vasquez, “Multiagent-based distributed state of charge balancing control for distributed energy storage units in ac microgrids,” IEEE Trans. Ind. Appl., vol. 53, no. 3, pp. 2369–2381, 2017.
- L. Xing, Y. Mishra, Y.-C. Tian, G. Ledwich, C. Zhou, W. Du, and F. Qian, “Distributed state-of-charge balance control with eventtriggered.
- M. Sharma, H. Elmiligi, F. Gebali and A. Verma, “Simulating Attacks for RPL and Generating Multi-class Dataset for Supervised Machine Learning,” 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 2019, pp. 0020-0026. keywords: {Feature extraction; Routing protocols; Wireless sensor networks; Machine learning; Correlation; Routing; Cyber Physical System; WSN security; WSN attacks; Routing Protocol for Low power and Lossy net-works(RPL);Feature Reduction (FR);Feature Engineering (FE);Information Gain (IG);Correlation based feature selection (CFS)}. [CrossRef]
- Mridula Sharma, Haytham Elmiligi, Fayez Gebali, Abhishek Verma, Simulating attacks for rpl and generating multi-class dataset for supervised machine learning, in: 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), IEEE, 2019, pp. 0020–0026.
- Sarumathi Murali, Abbas Jamalipour, A lightweight intrusion detection for sybil attack under mobile RPL in the internet of things, IEEE Internet Things J. 7 (1) (2019) 379–388.
- 2020; 58. Zahrah A Almusaylim, Abdulaziz Alhumam, Wathiq Mansoor, Pushpita Chatterjee, Noor Zaman Jhanjhi, Detection and mitigation of RPL rank and version number attacks in smart internet of things, 2020.
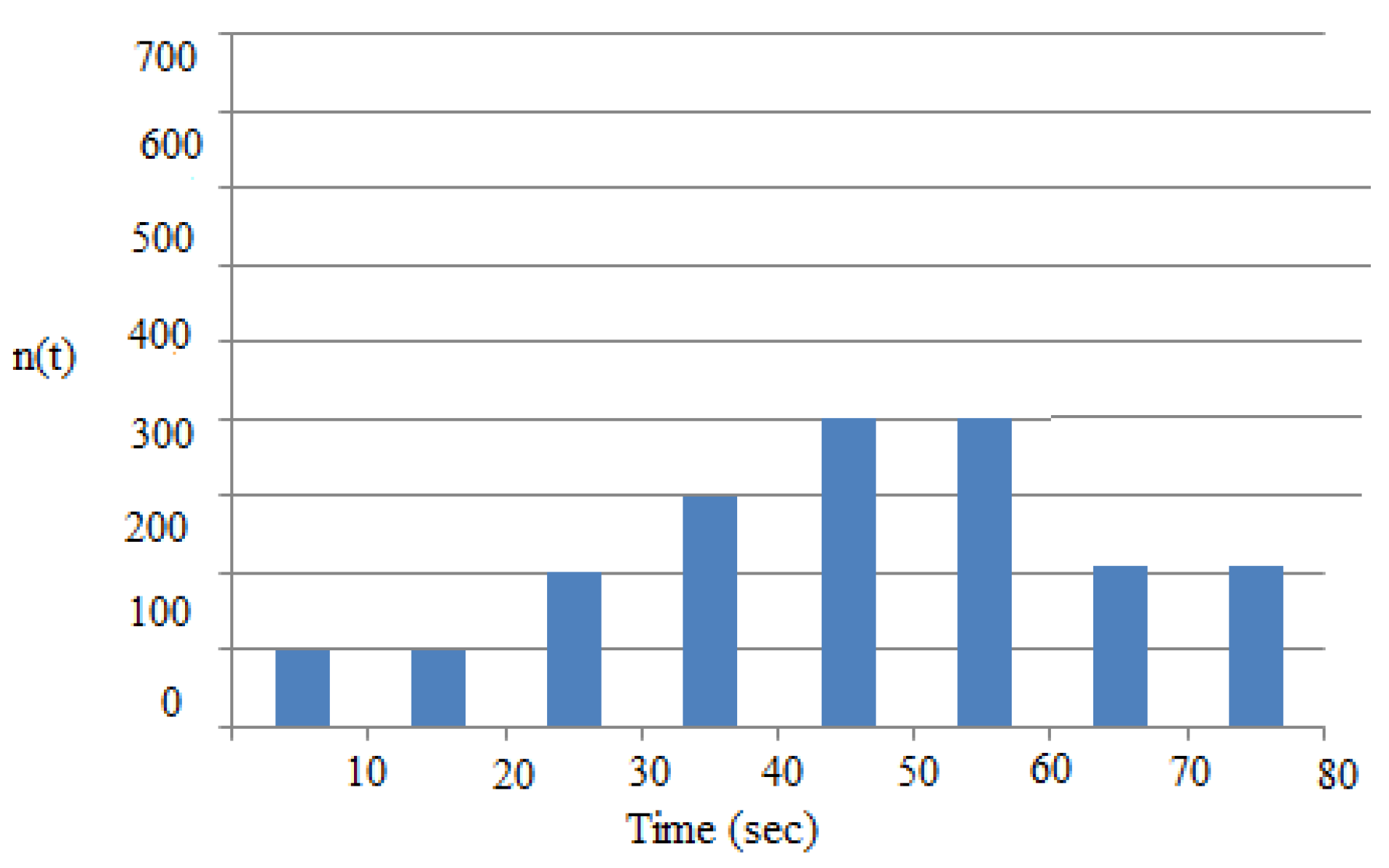
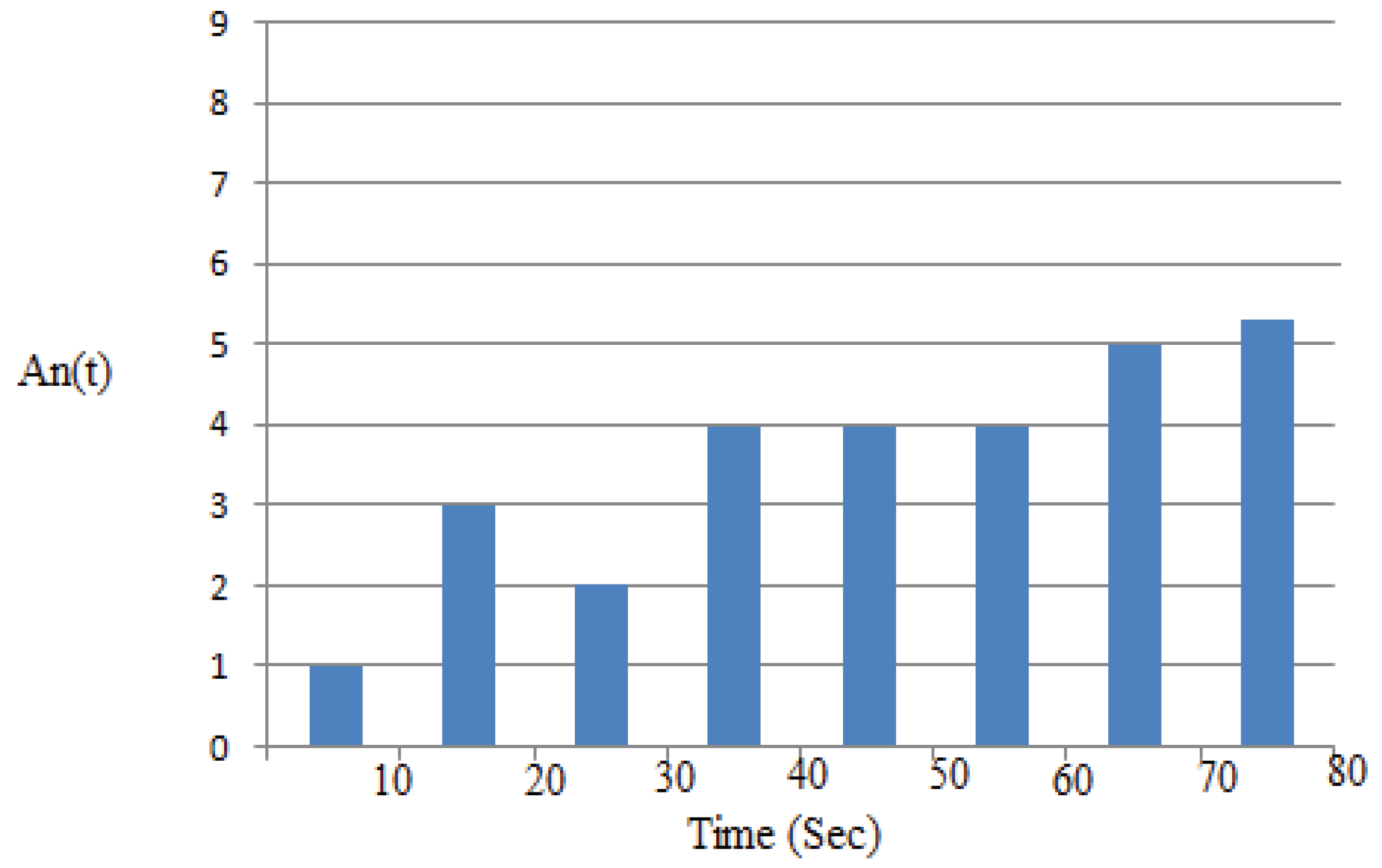
| N/S | Parameters | Value |
| 1 | Simulator | Cooja (Contiki 2.7) |
| 2 | Simulation time | 1800s |
| 3 | DODAG root rank | 1 |
| 4 | Scenario dimension | 200 * 200 m2 |
| 5 | Node Distribution | Uniform Distribution |
| 6 | Mote type | Z1 |
| 7 | Gateway nodes | 1 |
| 8 | Radio medium | Unit disk graph medium |
| 9 | Transport layer protocol | UDP |
| 10 | PHY and MAC layer | IEEE 802.15.4 |
| 11 | Data packet size | 30 bytes |
| 12 | Speed of node | 1 to 2 m/s |
| 13 | Transmission range | 50 m |
| 14 | Data packet sending interval | 60 s |
| 15 | Routing Protocol | RPL |
| 16 | Rank Metric | MRHOF |
| 17 | Nominal Capacity | 1000mAh |
| 18 | Battery Capacity | 1000mAh |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





