4. Cybersecurity Measure Implications
Strong security controls and cybersecurity training for employees are essential given the rising number of confirmed and suspected credential compromises [
58,
59] and their unmistakable link to attack success. Companies may need to ramp up their vulnerability management initiatives, tighten authentication procedures, and utilize continuous monitoring.
Table 1.
Summary Table of each resource tackling general attack types.
Table 1.
Summary Table of each resource tackling general attack types.
| Source/Participant |
Focus |
Approach/Style |
Emphasis |
| TechTarget Article |
Detailed types & prevention of
cyberattacks |
Structured list, case studies |
Practical measures, real-world examples |
| Geeks for Geeks Article |
Overview of cybercrime and its impacts |
Educational, overview-based |
Definitions, legal
aspects, basic prevention |
Academic Paper (AVOIDIT
Taxonomy)
|
Systematic
classification of cyber attacks |
Technical, research-oriented |
In-depth taxonomy
with multiple dimensions |
Narrative/Case Study
Video Transcripts
|
Step-by-step account of
multi-stage attacks |
Conversational,
storytelling |
Realistic depiction of
attack progression |
Finally with the sources identify malware (specifically ransomware), phishing, password attacks, DDoS, and injection attacks (SQL injection and XSS) as being among the most common forms of cyber-attacks. Various facts—such as the fact that there are an enormous number of attacks per week per organization, mean breach costs, and how important stolen credentials are to show that these are the most insidious threats to modern organizations and systems.
4.1. Overview of the Most Frequent Kind of Cyberattacks
The mentioned types of cyberattacks are oftentimes discussed and regularly seen, according to the source documents:
1. Ransomware: Extorts payment upon encrypting the victim’s data. Trojan horses, rootkits, and spyware are evil programs which pose as beneficial ones.
2. Phisher attacks: Spear phishing, whaling, and business email compromise (BEC) are methods of attack used to target emails in order to obtain sensitive data, such as login credentials.
3. Password attacks: Sniffing, dictionary, brute-force, and keylogging are methods of obtaining unauthorized access via exploiting weak or reused passwords.
4. Distributed Denial-of-Service (DDoS) attacks: Hundreds of millions of requests overwhelm network capacity, leaving legitimate users unable to utilize services. Injection attacks
5. Trojan code: can be injected into web applications using SQL Injection and Cross-Site Scripting (XSS) vulnerabilities.
6. Man-in-the-Middle attacks: intercept and alter two people’s conversations without either’s awareness.
4.2. Overview of Prevention Strategies
Table 2.
Overview of prevention strategies.
Table 2.
Overview of prevention strategies.
| Attack Type |
Key Prevention Strategies |
Malware
/Ransomware
|
Antivirus/anti-malware, email filtering, patch management, secure backups, user
awareness |
| Password Attacks |
Strong password policies, MFA, account lockout, regular password updates, user
training |
| DDoS Attacks |
Traffic filtering, rate limiting, load balancing, DDoS mitigation services, network
segmentation, continuous traffic monitoring |
| Phishing Attacks |
Email authentication (SPF/DKIM/DMARC), anti-phishing tools, browser security
alerts, employee training |
| SQL Injection |
Input validation, parameterized queries, code reviews, least privilege, WAFs |
Cross-Site
Scripting
|
Output encoding, input sanitization, CSP headers, regular security testing |
Man-in-the-
Middle
|
End-to-end encryption (SSL/TLS), VPN deployment, mutual authentication,
network segmentation, certificate management |
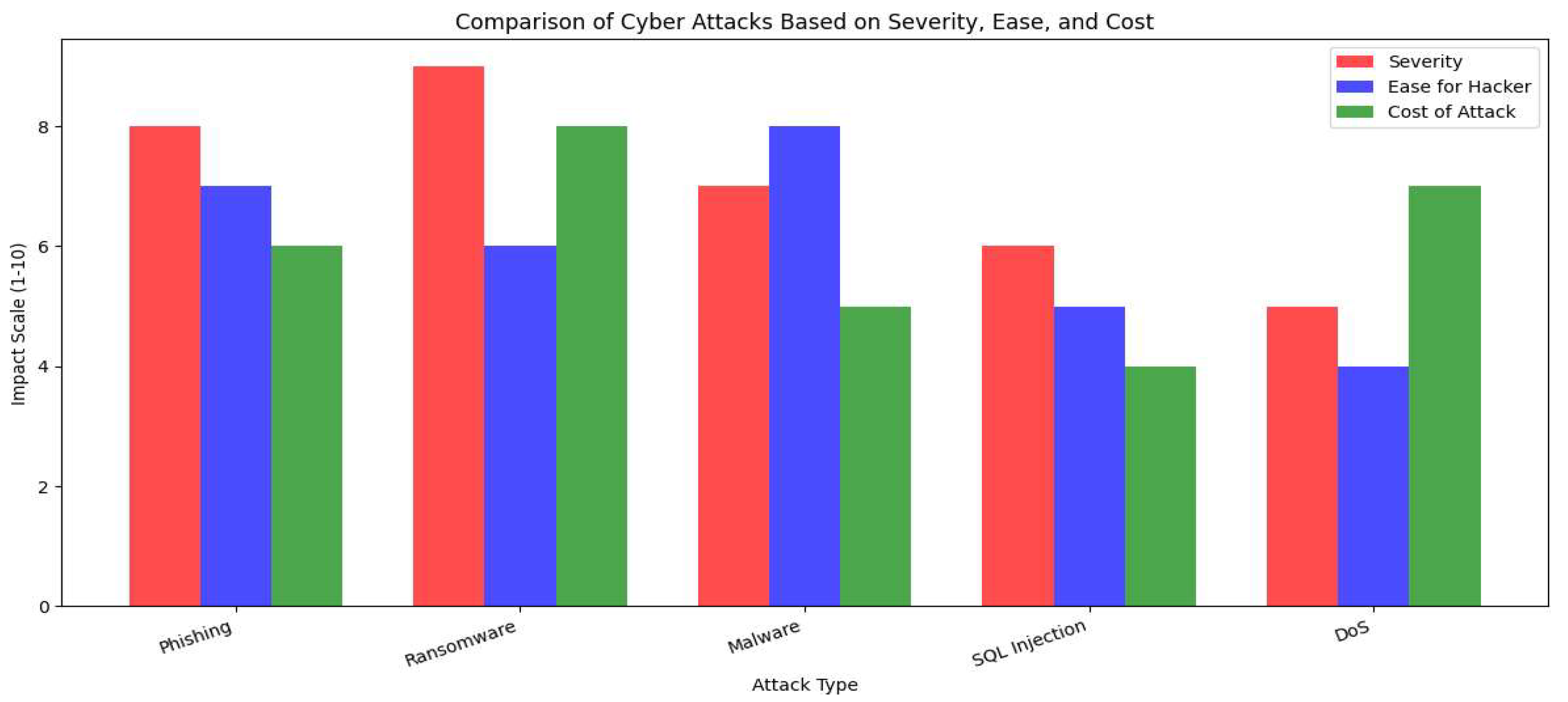
Ransomware, SQL Injection, and MITM are the most severe types of attacks due to the fact that they cause irreversible data loss, financial damage, and business interruption. Phishing, Password Attacks, and DDoS are the easiest attacks for hackers and, thus, the most common ones. They seldom require any sort of technical expertise but can still successfully produce serious consequences. Some of the costliest attacks to recover from are Ransomware attacks, DDoS attacks, and SQL Injection attacks. Malware that does this leaves serious downtime, legal penalties, and high costs of recovery. Of these, DDOS attacks are easy for the non-technical attacker, very hard to trace, not quite heavy enough to warrant serious countermeasures, and too painful to recover from financially; hence we can state that DDoS attacks are the worst type of cyber-attack.
Figure 2.
Comparison of Cyber Attacks in terms of Severity, Ease and Cost (Created in python via using insights extracted from sources by analysis tools).
Figure 2.
Comparison of Cyber Attacks in terms of Severity, Ease and Cost (Created in python via using insights extracted from sources by analysis tools).
These forms of malware and ransomware could cripple the functioning of an entire organization by encrypting critical files and demanding a hefty ransom for unlocking those files. Distributing these malevolent distractive programs could be achieved via phishing emails, infected websites, or by malicious downloads, thereby resulting in ransom payoffs, operational downtimes, extensive recoveries, and even huge reputational damage. Password attacks include brute-force attempts, credential stuffing, and phishing attacks, which are posing yet another serious threat because they facilitate unauthorized access, data theft, and identity fraud. An attack that does not involve physical intrusion is relatively easy to perpetrate, and recovery costs the victim severely depend upon sensitivity and accessibility of the compromised data.
Distributed denial of service (DDoS) attacks is one of the most potent threats to websites, services, or even an entire network because they overwhelm a target with traffic, usually from botnets and amplification techniques. An attack just like this may cause a company to go offline temporarily, directly resulting in revenue loss and possible physical damage to infrastructure. Phishing attacks still remain in the same category; they rely on the social engineering technique in persuading their victims to unknowingly reveal their credentials or financial account information to them, which is then subsequently used to further many other criminal acts like identity theft, financial fraud, malware infections, and penalties imposed for regulatory compliance failure. Such SQL Injection attacks typically destroy or at least expose total databases, giving ample opportunity for losing data, regulatory fines, and compliance violations. Poorly sanitized input allows the attacker to inject scripts into web applications; in this nature similar to SQL injection is cross-site scripting (XSS), where those injected scripts allow the attacker the ability to steal session data or redirect the user to malicious sites, but generally does not paralyze system-wide affairs. Finally, we have the critical threat of Man-in-the-Middle (MITM) attacks, intercepting and possibly altering communications between parties. Such breaches are usually beyond recovery and cause stolen credentials, financial losses, and compromised business communications.
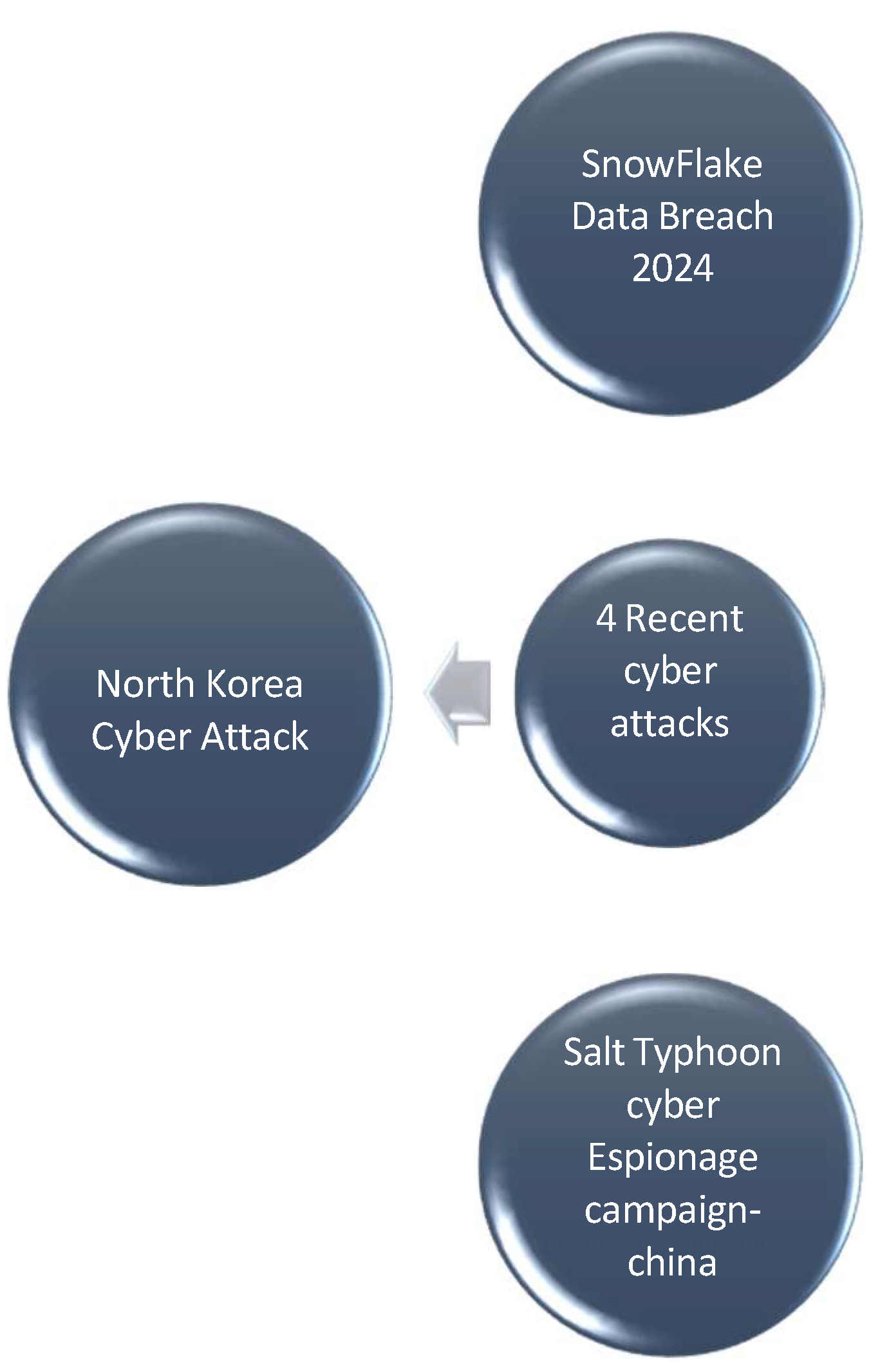
4.3. Specified Dangerous Cyber-Attacks That Took Place in Recent Times
The same is the case or rather they deal with all the four main departments in the company: marketing, finance, cybersecurity, and computer systems within the organization, thereby being involved at a corporate level. Knowledge of the integrated cyber-attacks that are occurring in the present times is useful when it comes to improving the defense line securing the private information of the institution. Some very vital cyber events illustrate how the scenario is constantly changing.
The first major incident is the Snowflake data breach of 2024, in which users of this cloud platform were targeted. Stolen user credentials were used for illegal access causing a serious breach that exposed sensitive customer information. The event is said to be serious for those organizations affected, with heavy financial losses as well as loss of reputation, thereby proving the risks of loose credential protection and mismanagement of cloud security [
44].
Another critical event included the ransomware attack on Change Healthcare in 2024. Cyber attackers exploited vulnerabilities in the company’s IT infrastructure, bringing about unprecedented service disruptions, disruption of patient care, loss of data, and significant financial loss [
45]. The event is noteworthy as it necessitates system monitoring in real-time and regular software updates in a bid to prevent ransomware attacks.
The third is the Salt Typhoon campaign, a state-led Chinese cyber-espionage campaign against key infrastructure since 2012. Phishing campaigns and advanced persistent threats (APTs) were used by Salt Typhoon to obtain access into government and telecommunications networks across the globe, exposing private data at risk and representing a significant national security threat. The attack highlights the need for improved email security and threat intelligence controls [
46].
The third attack involves North Korean cyber gangs that have been behind many politically and financially motivated cyberattacks. The cyberattacks were mainly against financial institutions and cryptocurrency exchanges, causing financial instability and raising global tensions by evading sanctions and supporting illegal activities. This attack shows the greatest necessity for efficient fraud detection systems and regulation of financial transactions.
4.4. Comparative Analysis of Cyber-Incidents
An overview of comparative cyber-incidents in the year 2024, focusing on some attacks initiated by hacker groups from North Korea, such as Snowflake and Change Healthcare, and the Salt Typhoon campaign, demonstrates how quickly and destructively modern cyber-targeting has become. All the incidents affecting Snowflake and Change Healthcare were ransomware attacks and data leaks that paralyzed their various operations and, notwithstanding, exposed sensitive information. In general, North Korean hackers and Salt Typhoon have remained focused on targeting financial theft and cyber-espionage activities.
Primary attack vectors for the Snowflake and Change Healthcare breaches included the following: compromised credentials and IT system vulnerabilities, which together culminated in unauthorized encryption and access of critical data. Differently, North Korean and Salt Typhoon hackers relied on such fail-proof phishing attacks, “advanced persistent threats,” and covert “living off land” techniques to infiltrate networks without detection. Prominently, Salt Typhoon focused on intelligence gathering by exploiting software vulnerabilities in critical infrastructures. By this, the consequences of these attacks have been harsh. One of the bangs shattered by the Snowflake breach concerns exposing the vulnerability of cloud security. It was disruption to healthcare services and huge financial costs that the great change caused for Change Healthcare. National insecurity in the Salt Typhoon campaign was compromised because sensitive government data leaked. North Korean attacks have further destabilized financial systems through cryptocurrency thefts.
4.5. Concerned Recommendations for Safeguarding XYZ Company from Cyber Threats
It will require a catch-all, multi-layered cybersecurity strategy for all departments—marketing, finance, cybersecurity, and computer-to protect XYZ Company against emerging cyber threats. Such departments should at least implement Zero Trust Architecture, which strictly enforces verification for any access requests before granting approval. The computer and cybersecurity teams shall employ robust multi-factor authentication (MFA) to ensure prevention of credential theft similar to the Snowflake incident. This will include the deployment of AI-enabled endpoint protection systems by the cybersecurity department to enable the systems detect unusual behavioral changes in real time, thereby capturing ransomware or APT activity before it worsens. Conduct regular security audits followed by the speedy patching of vulnerabilities, especially against weaknesses that are exploited in incidents such as Change Healthcare’s attack. In addition, programs on phishing awareness should be conducted to train all workers especially in the marketing and finance departments on social engineering attacks such as used in Salt Typhoon campaign. Tight network segmentation and access controls will restrict lateral movement in the hypothetical event of compromise, ensuring that each department has access only to the data they need.
Figure 3.
Recent cyber-attacks globally.
Figure 3.
Recent cyber-attacks globally.
There needs to be deployment of threat detection and behavioral analytics systems within the finance department that have the capability to detect abnormal financial transactions and prevent cryptocurrency thefts such as those conducted by North Korean hackers. To ensure that sensitive data is secured even in the event of a breach, data encryption and regular secure backups must be rendered mandatory in all critical systems. Lastly, XYZ Company must have a thorough incident response plan in place to contain and recover from cyber incidents quickly, with minimal disruption and organizational continuity. With these proactive and multi-layered cybersecurity measures, XYZ Company can more effectively protect itself from an ever-evolving hostile digital threat environment.
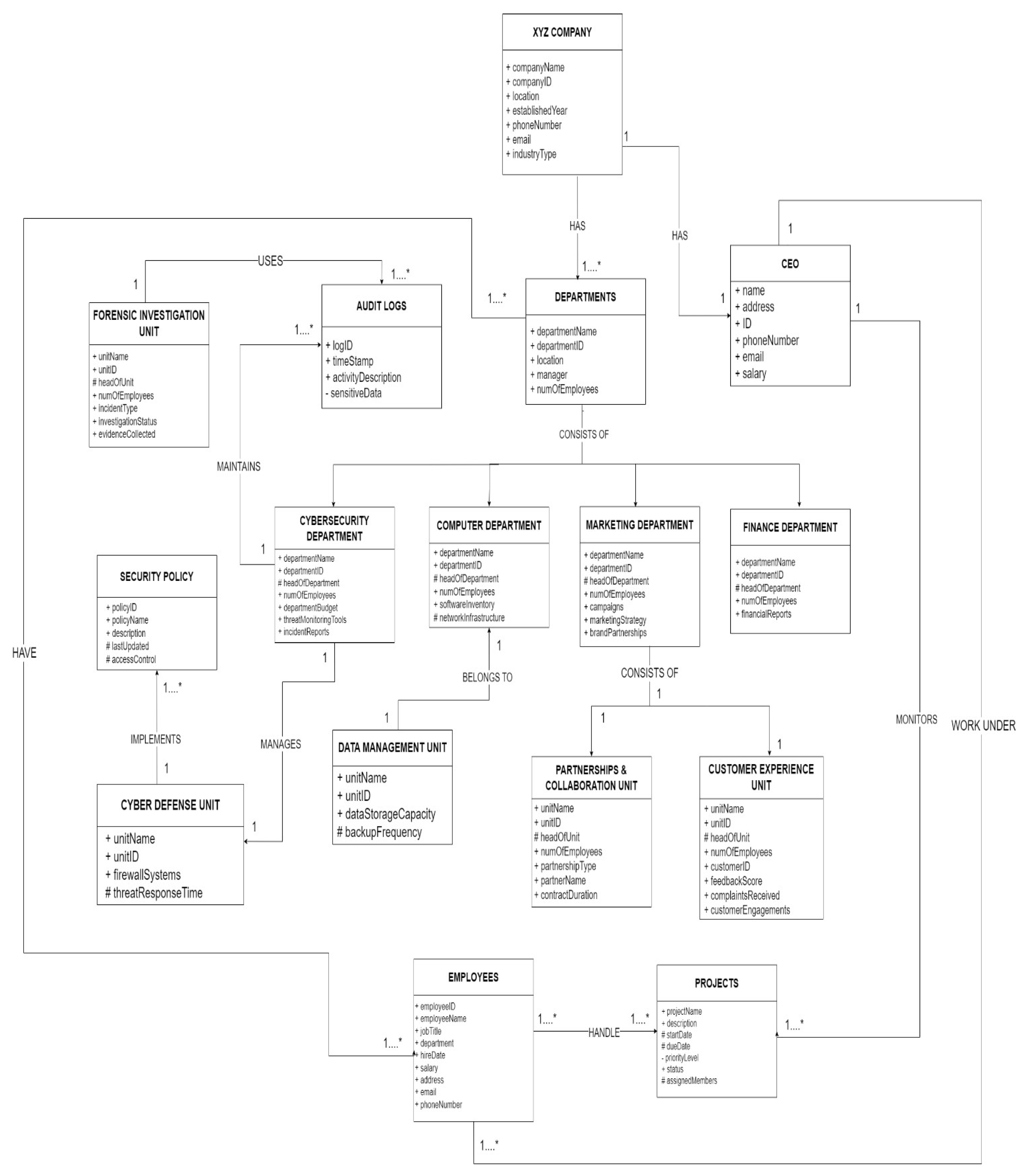
4.6. Organizational Taxonomy for XYZ Company
Figure 4.
UML Diagram for XYZ company.
Figure 4.
UML Diagram for XYZ company.
4.7. Organizational Taxonomy for XYZ Company
The XYZ Company is structured into four primary departments: Computer, Cybersecurity, Finance, and Marketing. The departments are all crucial in helping the company achieve its objectives while facilitating operational efficiency. The company utilizes a taxonomy approach to guarantee a well-defined representation of the hierarchical structure, illustrating relationships, attributes, and associations among the different components within the company. A detailed explanation of the taxonomy is given below:
4.8. Explanation of the Concepts and Relationships
Company and Departments (Association):
The XYZ Company is composed of several departments, each managing distinct operations. The relationship is classified as an association, indicating that departments are essential structural components of the company.
4.9. Departments and Corresponding Departments (Specialization)
The departments are divided into four distinct categories: Computer, Cybersecurity, Finance, and Marketing. The relationship is defined as specialization, meaning that each department is a more specific version of a general category within the company’s organizational hierarchy.
4.10. Departments and Employees (Association)
Employees are associated with specific departments, signifying that each department comprises multiple employees who are responsible for handling various projects and operational activities.
4.11. XYZ Company and CEO (Association)
The CEO holds an associative relationship with the entire company, overseeing all departments and leading strategic decision-making processes.
4.12. CEO and Projects (Association)
The CEO is in an associative relationship with company projects, always monitoring progress so that it is aligned with corporate goals and objectives.
4.13. Employees and Projects (Association)
The employees are held directly responsible for executing projects and making contributions to successful project implementation.
4.14. Employees and CEO (Association)
The employees are overseen by the CEO, where their contributions are aligned with the general organizational strategies and project requirements.
4.15. Data Management Unit and Computer Department (Association)
The Data Management Unit is located in the Computer Department and is tasked with conducting operations such as data storage, processing, and retrieval.
4.16. Relationship Between Cybersecurity Department and Audit Logs
Audit logs are important to monitor security-related activities. The Cybersecurity Department is responsible for updating and reviewing these logs to enhance the cybersecurity position of the organization.
4.17. Relationship Between Cybersecurity Department and Cyber Defense Unit
Cyber Defense Unit is a mission-critical sub-unit of Cybersecurity Department whose responsibility is deployment of defensive countermeasures to cyber-attacks and threats.
4.18. Security Policy (Association) and Cyber Defense Unit
Security policies, established and regulated by the Cyber Defense Unit, govern access to data and systems to ensure confidentiality, integrity, and security from potential damages.
4.19. Forensic Investigation Unit and Audit Logs (Association)
The Forensic Incident Investigation Unit investigates cyber violations via the process of gathering information electronically and relies massively on audit logs to keep an eye on patterns, follow security breaches, and assist the law enforcement authorities.
4.20. Marketing Department and Partnerships & Collaboration Unit (Specialization)
Partnerships & Collaboration Unit is a specialist marketing department unit engaged in forging relationships with foreign organizations, corporations, and government agencies to facilitate the development of the firm’s reputation along with increasing its horizon of market share.
4.21. Marketing Department and Customer Experience Unit (Specialization)
The Customer Experience Unit, again under the Marketing Department, is responsible for increasing customer engagement by understanding and meeting customer needs and expectations.
This categorization enables an integrated understanding of how different things—departments, employees, projects, and security measures—collaborate with one another. Embracing this organized strategy, XYZ Company can more effectively be able to control resources and safeguard data and operations from likely cyber-attacks.
4.22. Cognitive Computing for Enhanced Risk Discovery in LRMC
Cognitive Systems for Financial Risk Management: Overview
Cognitive systems are leveraging Artificial Intelligence (AI), Machine Learning (ML), and Big Data analytics to power operations in the financial services sector. Cognitive systems play a pivotal role in risk detection, predictive analysis, regulatory compliance, and improving overall decision-making processes. With the examination of massive amounts of structured and unstructured historical data, cognitive systems provide recommendations and predictions that help financial institutions reduce fraud, credit risk, and operational inefficiencies. As cyber-attacks and frauds get more advanced, the requirement for cognitive systems becomes more essential. AI and Big Data analytics supported by cognitive computing are most likely to play an important part in future financial risk management. Among the most advanced cognitive solutions, IBM Watson and Palantir Foundry stand out due to their robust infrastructure, verification capabilities, and eco-friendly measures.
4.23. IBM Watson: Finance-Driven Risk Management Through AI
IBM Watson is a robust AI-powered cognitive computing platform developed by IBM to assist organizations in handling risk and compliance with regulatory requirements. IBM Watson uses ML and Natural Language Processing (NLP) to analyze structured and unstructured financial data like risk reports, regulatory reports, and historical case studies to generate actionable insights into risk management (IBM, n.d.). It has been widely utilized by financial institutions to address fraud detection, credit risk assessment, and regulatory compliance issues and therefore is a highly relevant solution for improving financial risk management practices in Malaysia.
4.24. IBM Watson Capabilities for Risk Management
AI-Powered Risk Insights:
IBM Watson applies ML and NLP to process large financial data sets to identify early warning signals of risk. For example, CitiBank uses Watson to scan millions of transactions and detect fraudulent transactions in real-time, enabling proactive risk mitigation.
4.25. Automated Compliance Management
Watson governs and monitors adherence to financial regulations such as Basel III, IFRS 9, and Anti-Money Laundering (AML) regulations. HSBC has integrated Watson to simplify monitoring of compliance processes for automation, reducing manual workloads and enhancing regulatory compliance, particularly in Bank Negara Malaysia’s system.
4.26. Predictive Analytics
IBM Watson’s predictive analytics capabilities examine credit risks, market volatility, and fraud trends. BNP Paribas leverages these capabilities to examine lending risks and support financial decision-making processes.
4.27. Cognitive Automation:
Watson performs tasks such as policy assessment, fraud detection, and risk analysis. For example, ANZ Bank employs Watson to automate loan application processing, accelerating processing times and boosting operational efficiency.
4.28. Integration Capabilities:
IBM Watson can be seamlessly integrated into existing financial IT infrastructures, including Enterprise Resource Planning (ERP) systems, risk management systems, and regulatory data bases.
4.29. IBM Watson Benefits
Anticipatory Identification of Risk:
Watson empowers banks and financial institutions to recognize risk and act beforehand by means of artificial intelligence-powered analysis. Deutsche Bank utilizes Watson in order to project risks to markets and reallocate investment planning accordingly.
4.30. Deterring Non-Compliance
IBM Watson keeps institutions informed of evolving global and domestic financial rules and regulations and prevents them from incurring legal fines and reputational damage. Standard Chartered Bank uses Watson for AML control in various countries.
4.31. Improved Decision-Making
IBM Watson, on the basis of risk analysis driven by data, enables financial institutions to make highly informed business decisions. For instance, UBS uses Watson to handle client portfolios and tailor investment policies.
4.32. Operational Efficiency
With automation of routine risk assessments and compliance processes, IBM Watson can release human capabilities for value-add activities. Automation of customer service and real-time risk monitoring is employed by DBS Bank in Singapore via Watson to enhance both efficacy and quality of service.
4.33. Limitations of IBM Watson
1. High Implementation Cost: For deploying IBM Watson, there is enormous initial investment in hardware, training the artificial intelligence, and configuring underlying software. Long-term returns made high initial expenditures worth investing in using Watson as a component of JP Morgan’s risk management infrastructure.
2. Advanced Customization: In the first place, Watson’s AI models can be tailored to particular financial risk scenarios, a time- and resource-consuming activity. To adapt Watson to its (the bespoke) risk assessment needs, Barclays spent months training Watson’s AI models.
3. Data Privacy Concerns: For financial institutions, robust data protection compliance takes precedence, similar to in the instance of regulatory frameworks such as Malaysia’s Personal Data Protection Act (PDPA), or GDPR. With respect to putting Watson to work with sensitive financial transactions, ING Bank had to introduce added cyber security controls.
4. Reliance on Data Quality: Accuracy and completeness of data significantly influence what IBM Watson will predict or insight into. A problem for Wells Fargo stemmed from missing or contradictory data leading to incorrect risk determinations.
4.34. Palantir Foundry: Extremely Sophisticated Data Integration to Reduce Risk
Palantir Foundry is an analytics and integration platform that is mainly designed to allow organizations to manage complex and large volumes of data, enhancing decision-making process. With the application of artificial intelligence, machine learning and big data tools, this platform forms a strong model to identify, manage and assess the risk. Its predictive modeling algorithm enables the companies to examine their past data and generate future forecasts regarding their steps. This forecasting facility becomes essential in the context of a risk management system for any firm since firms gain their insight and the company’s future forecasting due to decisions made. Benefits are real-time risk monitoring system, fraud detection, regulatory compliance among many others. According to the Palantir foundry risk management framework, businesses around the world can enhance their operations efficiency and company’s financial stability.
4.35. Palantir Foundry Features for Risk Management
Palantir Foundry has a number of sophisticated capabilities which make it ideal for financial risk management. One of its greatest capabilities is Unified Data Integration, whereby the risk models, transactional data, regulatory reporting, and data sources are all combined on one platform. This integrated approach enhances the pace of risk analysis by allowing for in-depth data visibility and seamless operations. Another key ability is AI-Powered Risk Analysis, whereby the platform uses machine learning and artificial intelligence models to examine historical data, recognize patterns, and uncover potential risks. Foundry also provides detailed reports and actionable recommendations, enabling companies to make informed decisions.
Regulatory Compliance Automation is another key ability, enabling financial institutions to meet requirements under regulations like Basel III, IFRS 9, and Anti-Money Laundering (AML) legislation. With automated compliance tracking, the platform reduces human error and maintains regulatory compliance. Additionally, Palantir Foundry provides Real-Time Risk Monitoring, which helps industries monitor financial market trends in real-time and respond to increasing risks proactively. Further, its Scalable and Customizable Infrastructure enables organizations to tailor risk models and workflows according to individual institutional needs, providing the flexibility necessary for growing and changing infrastructure.
4.36. Benefits of Palantir Foundry
Palantir Foundry offers numerous benefits to organizations looking to improve their financial risk management. A major benefit is Enhanced Risk Identification since the AI-driven analytics allow businesses to spot risks before they happen, and hence safeguard assets and reduce risk exposure. Better Regulatory Compliance is also facilitated through the platform via auto-enabled processes and reduced risks of breaches and associated legal problems. Another significant advantage is Data-Driven Decision Making, whereby the historic and real-time data available to institutions enables the making of adequately supported, fact-based financial choices.
End-to-End Data Integration and Transformation is a unique advantage as Foundry successfully pulls together structured data and unstructured data from diverse sources and enables consistent operations. Granular Access Control and Data Security is also highly prioritized, with hyper-granular permissions enabling hard controls over access to data as well as how it is processed. Additionally, Foundry contains No-Code/Low-Code Pipelines that allow users who are not technical to construct data transformation flows through simple drag-and-drop interfaces, thereby reducing reliance on technical staff and accelerating operational processes. Lastly, Palantir Foundry is notable for its Military-Grade Security and a Demonstrated Track Record in defense and intelligence organizations, having been broadly utilized by government agencies like the CIA and the U.S. Department of Defense for sensitive missions.
4.37. Limitations of Palantir Foundry
While it is rich in advantages, Palantir Foundry also has some disadvantages. High Implementation and Maintenance Cost is perhaps the largest disadvantage. Its installation, infrastructure, environment, training, and customization are too expensive, restricting the platform primarily to large institutions such as Morgan Stanley and Goldman Sachs, since small companies cannot afford its expense. Another disadvantage is the Complexity of Integration with Legacy Systems. The implementation of Palantir Foundry together with other financial technology infrastructures is cumbersome and challenging, as was the case with the case of UBS that suffered a few months of adaptation challenges.
The platform also exhibits a Steep Learning Curve. Although facilitated by no-code/low-code capabilities, intense customization requires deep technical expertise, thus posing difficulties for risk analysts and financial managers who are non-technical. Lastly, Data Privacy and Regulatory Concerns are major concerns. Because of the sensitive financial data handled by Foundry, institutions such as Credit Suisse have been forced to employ additional encryption and cybersecurity to meet stringent regulatory standards such as GDPR, PDPA, and Basel III compliance.