1. Introduction
Ensuring information security is an important task in the modern world. The main functions of the SOC and CSIRT teams are timely response to information security incidents and their prevention, as well as timely detection of vulnerabilities, threats, and risks in the system and their processing.
CSIRT teams face certain difficulties when performing information system (IS) risk assessments. First, at the stage of planning and building certs and related processes, it is difficult to take into account all the risks associated with the IS in which they will work. Secondly, there is no time- and cost-efficient risk assessment method. The team needs to assess the risks of an ongoing attack or identified vulnerability as soon as possible and make quick decisions on how to mitigate the risks.
Third, explaining to other departments involved in CSIRT processes the criticality of a particular vulnerability and the need to take countermeasures to minimize the risks is a challenge. Because it can be difficult for legal, administrative, and security departments to understand technical risk analysis reports due to the lack of a standardized way of presenting this information. The challenge is that management does not always understand complex technical risk reports, and there is no appropriate method to communicate infrastructure risk information clearly and visually to senior management.
This paper discusses information security risks associated with the use of Data Leakage Prevention (DLP). We propose a combined risk assessment method to efficiently and quickly assess risks when new vulnerabilities are discovered in IS in an environment in which information security incident response teams are operating. This can enable the prioritization of risks and the order in which certs should notify customers of a discovered vulnerability. The stage at which categorization, criticality level determination, and assessment take place. CSIRT teams also deal with targeting IS attacks. Unfortunately, it is not always possible to incorporate these attacks into threat models due to their unpredictability and complexity. That is, the teams lack methods that would allow them to effectively determine the level of risk associated with advanced, targeted attacks. To solve this issue, a method based on expert assessments using risk-oriented patterns is proposed. Moreover, security teams need to conduct risk assessments within their IS and infrastructure to eliminate possible cybersecurity threats.
This will help identify information security risks associated with using technical means before the commissioning of informationization facilities. Moreover, this method may be suitable for business process modeling specialists, who can assess information security risks in advance to identify potential vulnerabilities and determine priority. Information security risk-oriented patterns are the best way to convey the necessary information clearly and easily, for example, the technical aspects of an information system, to all interested parties who are in any way connected with this IS. Business process modeling experts have limited experience in the information security area.
A literature review was conducted for our research. Article [
1] examines automation in security operations centers (SOCs) and its impact on analysts. The authors highlight issues such as automation bias and complacency that arise as analysts become increasingly dependent on automated tools.
Research [
2] proposes an adaptive risk management approach to counter privacy attacks in Fog-IoT environment. The authors highlight the importance of integrating edge computing (fog computing) into IoT to reduce latency, increase geographic distribution, and local data processing. [
3] discusses a security assessment framework that combines two different multi-criteria models with the goal of finding interconnections between security criteria with further prioritization. Paper [
4] describes the improvement of the threat modeling technique with the involvement of a number of master’s students with the goal of evaluating the completeness and correctness of the results analysis.
The objective of research [
5] is to determine the security conditions of e-banking applications and analyze the risks and threats that can happen to customers.
Work [
6] examines the problem of insider threats in the healthcare industry using text mining techniques to identify and prevent potential risks. The authors emphasize the importance of protecting patients’ confidential information and propose using text mining to monitor and detect abnormal employee actions that may pose a threat to data security.
Many research papers have been written about risk determination, security, and reliability by implementing multi-criteria methods in different practical spheres [
7,
8,
9,
10]. In [
11]–14], the problems of information security and reliability were researched, methods providing security and reliability for identification and mitigating security risks at the initial phase of IS construction were suggested, and a suitable software system was constructed on the basis of the suggested methods.
In [
15], a method for automatic sorting, containment, and escalation for SOC is proposed.
2. Materials and Methods
Sorting in the context of information security refers to the process of prioritizing incident resolution based on the severity of a security breach or compromise. Triage in the context of information security incident response is the primary processing and screening of cybersecurity incidents. The proposed method can help CSIRT and SOC in these two processes (triage and sorting) to handle cybersecurity incidents and make further analyses for the determination of security risks connected to cybersecurity incidents. In this article, according to the method, assessments are made partially by experts and partially using the CVSS method. This method involves using security risk-based BPMN to identify system and business assets, security threats related to IS components, and countermeasures for them with further risk assessment by means of expert interviews. The use of risk-oriented model BPMN visually helps to identify, sort, and assess risks. Our method helps prioritize vulnerabilities without resorting to complex technical tools. CSIRT may provide a new service to check ensurance of the security and reliability of information systems by applying risk assessment according to the proposed method. This method can be applied to prioritization of information security risks and determining information security requirements.
Let’s consider the next scenario: when the CSIRT or SOC receives several security incidents at once, it is crucial to determine the order of response to them since it is not always possible to handle incidents in parallel. In this way, the method can be applied at the initial stage of incident processing - identify the assets involved in the incident, determine the vulnerabilities that the attacker exploited, and come up with a way to eliminate the threat. And, of course, it is best to visualize each step using BPMN. Next, in order to prioritize incident response, it is necessary to assess the risks that these IS incidents may pose.
The next way how the proposed method can be used is to implement it at the stage of building processes and information and communication infrastructure of CSIRT or SOC. That is determination using risk-based BPMN of system and business assets of future information and communication infrastructure, possible vulnerabilities and threats to information security of assets that may arise, and how to counteract the emerging cyber threats. Further, according to the method - to assess the risks that may occur after the construction of CSIRT and SOC, and if necessary - to eliminate them depending on the level of criticality of the risk.
According to the method, the first step is to describe the organization’s assets that need protection and determine the security criteria with the goal of security risk assessment. At this stage, business assets and system assets are allocated, and security goals are determined. Metrics such as value and security requirements are defined. Business assets mean events, tasks, and data objects. System assets mean data storage, containers - independent units of the process, and organizational units (for example database, program, and IS components).
Let’s consider the application of the risk assessment method in the example of DLP-related infrastructure. DLP system is a tool that CSIRTs often use as part of their core business. Therefore, the risk assessment will help to identify the main gaps, weaknesses in the security of this DLP system and prevent possible information security incidents related to various vulnerabilities.
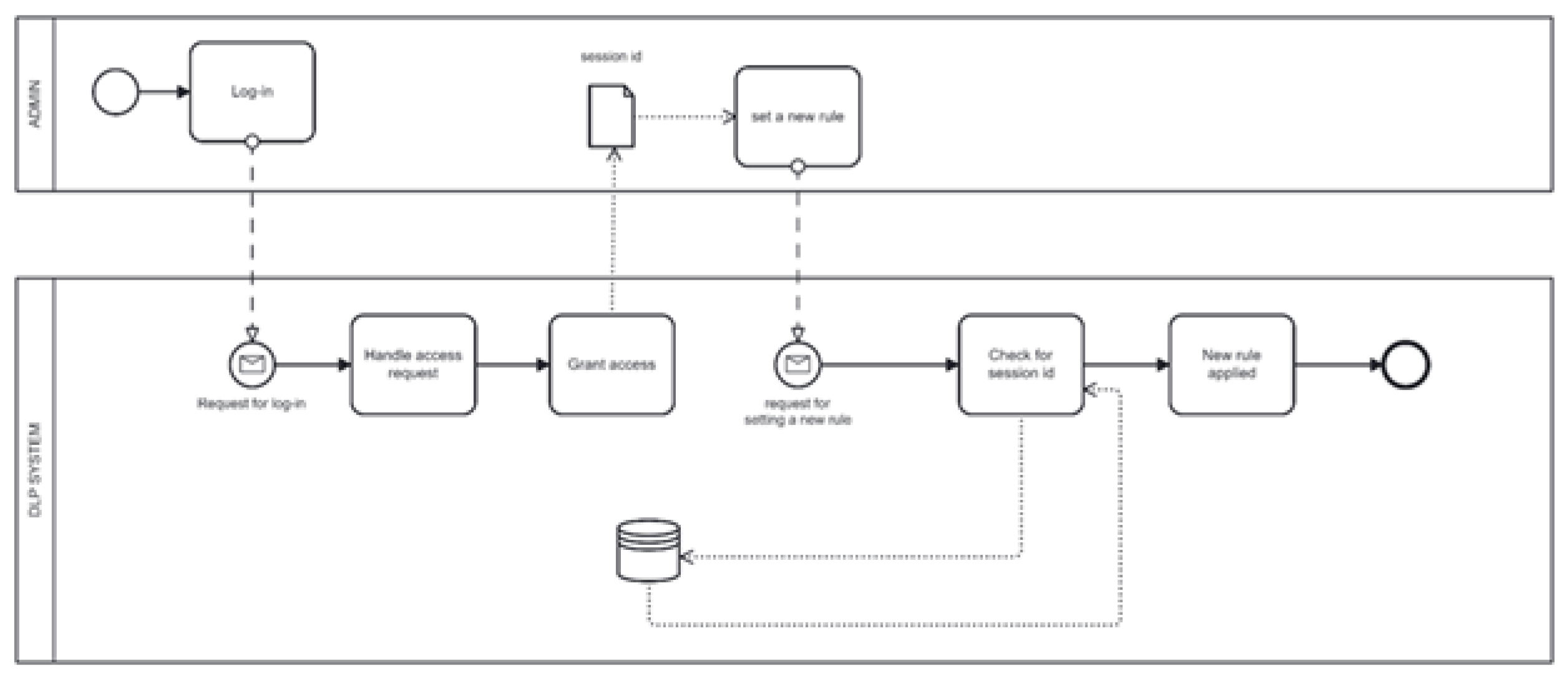
Figure 1 shows business assets, system assets, and IS assets. It describes the authorization process of an administrator in the DLP system. The DLP system processes the username and password entered by the user. If the password and username match, it grants administrator privileges and gives this user a specific session identifier.
Next, concepts related to information security risks are used to identify these risks and their components. Risk-based BPMN is utilized to show the violator’s actions, vulnerabilities in the system, and other activities that aim to achieve desired results. The risk value is determined with the help of the risk level metric. It is important to map the details of the risk as closely as possible so that experts can understand what the risk is about, how it occurs, what consequences and threats the risk may carry, and more accurately assess metrics such as risk level, impact level, potentiality and probability of risk. The CVE vulnerability database was used to describe the risks.
Thus,
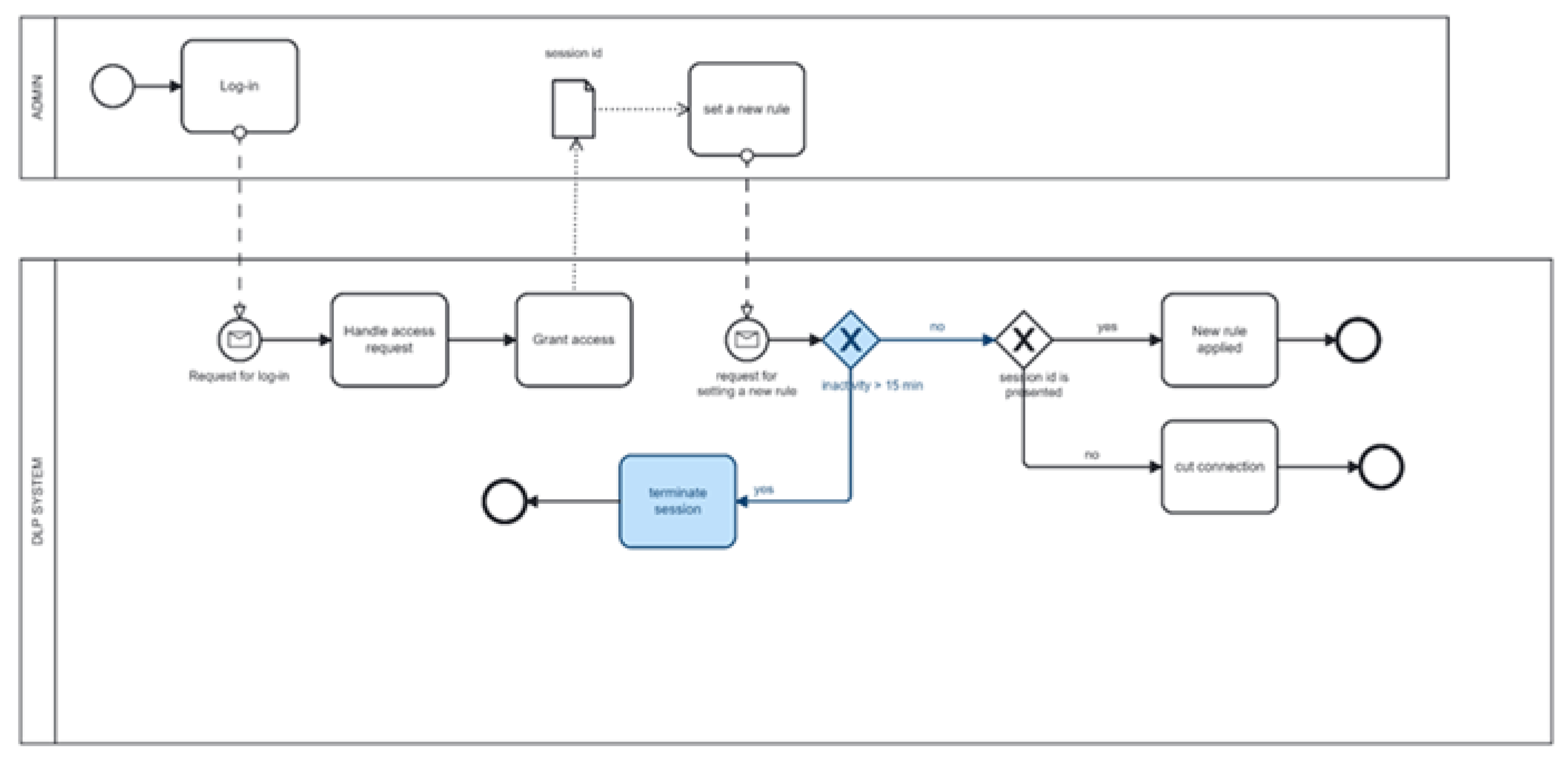
Figure 2 shows the risk associated with a vulnerability in the DLP, which can occur due to improper session management. An attacker can use this vulnerability to gain the privileges of the DLP system administrator and gain further access to confidential documents. The figure shows that an attacker can use a brute force attack to select a session ID and act on behalf of the administrator due to a vulnerability in the DLP system.
Figure 3 shows the method of applying countermeasures to the actions of the violator described above. These countermeasures reduce the risk. To ensure that the session on the server is terminated when the user logs out, it is proposed to implement an "inactivity timeout" for each session.
Further, risk assessment and analysis take place after determining the risks.
Risk assessment is conducted by experts. Experts are invited to review the questionnaire, which presents questions that will help them obtain certain scores for a particular metric and ultimately help to assess each risk and conduct further analysis. As a result assessments of security need, cost, value, threat likelihood and vulnerability level were obtained.
Some of the questions from the questionnaire that were given to the experts:
What score will you set for the value parameter for this asset?;
Evaluate the impact on the confidentiality metric for the session ID asset;
Evaluate the impact on the integrity metric for the session ID asset;
Evaluate the impact on the availability metric for the asset session ID;
Evaluate the vulnerability level metric;
Rate the threat likelihood metric.;
Evaluate the cost metric (the cost of implementing these countermeasures);
How much do you think it will cost to implement these countermeasures?;
The average values of expert estimates were calculated for value, security need, threat likelihood, cost, and vulnerability level.
As a result, experts evaluated only seven metrics. The other two metrics were automatically received using the CVSS method. The rest of the metrics were calculated based on previously assessed metrics.
And now about how the points were assigned. The questionnaire asked each BPMN diagram to be scored for specific metrics. For example, under the diagram depicting the model of context and asset, it was proposed to assign points for the value of assets from 1 to 5 and also to assign points for 3 metrics of security need, namely, confidentiality, availability, and integrity, in the range from 1 to 3. Under the diagram of the security risk model in the questionnaire, experts were asked to give points for the metrics vulnerability level from 1 to 10 and for the metric probability of threat to give points from 1 to 10. Below the countermeasures model diagram, experts were asked to score the cost of countermeasures metric from 1 to 10.
The event potentiality metric was calculated as probability plus vulnerability level minus one. The impact metric was obtained through the security need metrics by finding the maximum of the three metrics. The risk level metric is calculated based on the other two metrics by multiplying event potentiality by the impact.
The risk reduction level is obtained as risk level 1 (risk level before countermeasures) minus risk level 2 (risk level after countermeasures). CVSS was used to calculate vulnerability level and threat likelihood metrics after taking countermeasures. Thus, the assessment method is combined and consists of two methods – expert and CVSS.
Metrics such as vulnerability level after treatment and threat likelihood after treatment are assessed using the program method CVSS. This method makes assessment of estimated metrics much easier and more precise. It’s hard to completely convey and depict all the nuances of IS using risk-oriented models. Therefore, an assessment made using a risk-oriented BPMN can sometimes turn out to be rough. Assessing countermeasures requires knowledge of the specifications and peculiarities of IS and how IS can behave after security risk decreases, especially in the planning stage. Companies can’t provide detailed IS diagrams for some considerations. For this reason, it will be a little bit hard for external experts who are involved in other departments or organizations to assess it precisely. It is suggested to use the CVSS method together with expert assessment, which can help assess security risks more precisely, save time and increase efficiency.
For our combined method of security risk assessment, we used the base score metric and exploitability subscore metrics from the CVSS framework.
3. Results
Table 1 presents other risk-based models for the remaining risks for convenience. These models are determined analogically by the method described above.
After calculating all the metrics, an analysis based on the data was carried out to identify the risk with the highest priority.
The priority of response to incidents connected with discovered vulnerabilities, i.e., security risks, has very important meaning for computer emergency response teams. Thus, it is necessary to understand which risk should be reflected first. For these goals, the trade-off analysis is conducted using the risk reduction level (RRL), countermeasure’s cost, and business asset value obtained from expert assessment.
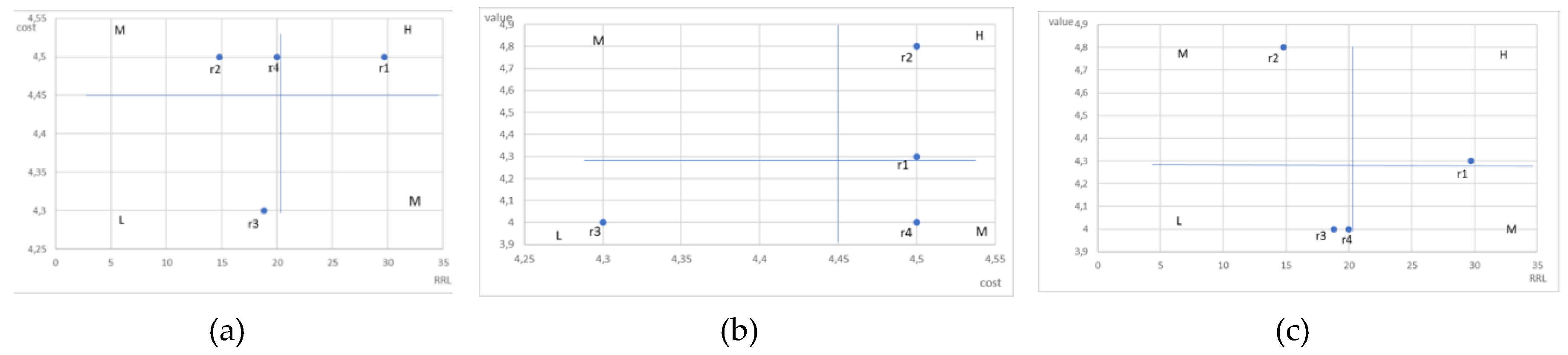
Utilizing these metrics, three graphs were accomplished (see
Figure 4(a), 4(b), and 4(c)) incorporating data on cost and RRL, value and cost, value and RRL. The graphs are divided into four quadrants, and the priority for each quadrant is identified by labels low (L), medium (M), and high (H) on each quadrant. From an incident response perspective, the cost of countermeasures refers to the amount of human and programmatic resources that must be used to eliminate an attack or incident. By the value of the cost, it is possible to conclude the magnitude and severity of the risk. A high value of an asset implies that a lot of work will have to be done to eliminate the incident if the risk is realized, from which we can conclude that the risk is critical. Its elimination becomes a higher priority than a risk with a lower value. From the Incident Response point of view, the value of the Risk Reduction Level can be used to infer the criticality of the risk and the appropriateness of the response to the incident. The higher the value, the greater the effect of responding to the incident and, thus, the more appropriate it is to respond to the security incident in the first place. This makes the risk a higher priority for incident response teams. Of course, the higher the asset’s value, the more the CSIRT or SOC prioritizes it when responding to incidents.
Figure 4(a) presents a graph of the cost against the level of risk reduction.
According to the graph, Risk 1 (r1) is high priority, Risk 2 (r2) and Risk 4 (r4) are middle priority, and Risk 3 (r3) is low priority.
Figure 4(b) is about the business asset value against the cost of countermeasure. According to the graph, Risk 2 (r2) and Risk 1 (r1) are a high priority, and Risk 4 (r4) has a low priority.
Figure 4(c) is about the asset value against the risk reduction level. According to the graph, Risk 1 (r1) is a high-priority risk, Risk 2 (r2) is a middle-priority risk, Risk 3(r3) and Risk 4(r4) are low-priority risks.
Then, according to the diagrams, the total score for each risk was calculated. If the risk falls into area H, then 3 points are awarded, if it falls into area M, then it gets 2 points, if it falls into area L, then 1 point is awarded. As a result, after calculations, it turned out that risk 1 has the highest priority, risks 2 and 4 have medium priority, and risk 2 has the lowest priority.
4. Discussion
In this article, a combined method of IS security risk management is proposed, which is based on expert assessments. This method can be applied to prioritize information security risks at the stage of sorting information security incidents, and to determine information security requirements when modeling IS processes. Sorting in the context of information security refers to the process of prioritizing incident resolution based on the severity of a security breach or compromise. The response teams sort through the incidents that have already occurred. This article proposes a method based on expert assessments using risk-oriented patterns to manage IS security risks. Information security risk-oriented patterns are the best way to convey the necessary information clearly and easily, for example, the technical aspects of an IS, to all interested parties who are in any way connected with this IS. Using this method can visually help identify, sort, assess risks, and prioritize vulnerabilities without the use of technical means.
The proposed method is considered when modeling attacks on information security systems against leaks. The priorities of the risks associated with these attacks have been identified. Such systems can be used in SOC and CERT work. Therefore, the method can be applied when building business processes related to SOC and CERT.
Abbreviations
The following abbreviations are used in this manuscript:
| SOC |
Security Operations Center |
| CSIRT |
Computer security incident response team |
| DLP |
Data Loss Prevention |
References
- Tilbury, J.; Flowerday, S. Automation Bias and Complacency in Security Operation Centers. Computers 2024, 13, 165. [Google Scholar] [CrossRef]
- Selvan, S.; Mahinderjit Singh, M. Adaptive Contextual Risk-Based Model to Tackle Confidentiality-Based Attacks in Fog-IoT Paradigm. Computers 2022, 11, 16. [Google Scholar] [CrossRef]
- K. C. Park and D.-H. Shin, “Security assessment framework for iot service,” Telecomm. Systems, vol. 64, no. 1, pp. 193-209, Jan. 2017. [CrossRef]
- R. Scandariato, K. Wuyts, W. Joosen, “A descriptive study of Microsoft’s threat modeling technique,” Requir. Eng., vol. 20, no. 2, pp. 163–180, June 2015. [CrossRef]
- G. Mogos and N. S. Mohd Jamail, “Study on security risks of e-banking system,” Indones. J. Electr. Eng. Comput. Sci., vol. 21, no. 2, pp. 1065–1072, Feb. 2020. [CrossRef]
- Lee, I. Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach. Information 2022, 13, 404. [Google Scholar] [CrossRef]
- Collen, A.; Szanto, I.-C.; Benyahya, M.; Genge, B.; Nijdam, N.A. Integrating Human Factors in the Visualisation of Usable Transparency for Dynamic Risk Assessment. Information 2022, 13, 340. [Google Scholar] [CrossRef]
- Khan, A.N.; Bryans, J.; Sabaliauskaite, G.; Jadidbonab, H. Integrated Attack Tree in Residual Risk Management Framework. Information 2023, 14, 639. [Google Scholar] [CrossRef]
- Alsafwani, N.; Fazea, Y.; Alnajjar, F. Strategic Approaches in Network Communication and Information Security Risk Assessment. Information 2024, 15, 353. [Google Scholar] [CrossRef]
- A.M AbdelMouty, A. Abdel-Monem, “Neutrosophic MCDM Methodology for Assessment Risks of Cyber Security in Power Management,” Neutrosoph. Systems Appl., vol. 3, pp. 53-61, Mar. 2023. [CrossRef]
- Villegas-Ch, W.; Ortiz-Garces, I.; Sánchez-Viteri, S. Proposal for an Implementation Guide for a Computer Security Incident Response Team on a University Campus. Computers 2021, 10, 102. [Google Scholar] [CrossRef]
- Portase, R.M.; Colesa, A.; Sebestyen, G. SpecRep: Adversary Emulation Based on Attack Objective Specification in Heterogeneous Infrastructures. Sensors 2024, 24, 5601. [Google Scholar] [CrossRef] [PubMed]
- Metin, B.; Duran, S.; Telli, E.; Mutlutürk, M.; Wynn, M. IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture. Information 2024, 15, 55. [Google Scholar] [CrossRef]
- Kim, I.; Park, M.; Lee, H.-J.; Jang, J.; Lee, S.; Shin, D. A Study on the Multi-Cyber Range Application of Mission-Based Cybersecurity Testing and Evaluation in Association with the Risk Management Framework. Information 2024, 15, 18. [Google Scholar] [CrossRef]
- Danquah, P. Security Operations Center: A Framework for Automated Triage, Containment and Escalation. J. Inf. Sec. 2020, 11, 225–240. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).